User manual
Table Of Contents
- Table of Contents
- About This Guide
- Introduction
- ISDN LAN Modem Functionality Description
- Hardware Description and Installation
- Setting Up TCP/IP for Windows and Macintosh
- Configuring the ISDN LAN Modem
- Advanced Configuration
- Before you Begin
- Setting Up Additional Service Providers
- Editing Service Provider Profiles
- Restricting Workstations from Accessing Service Provider(s)
- Configuring Your LAN Parameters
- Changing Data Call Parameters
- Changing Voice Call Routing
- Reserving DHCP Addresses
- Selective Password Protection
- Changing Your Password
- Setting Up Your ISDN Line Manually
- Locking and Unlocking the Configuration
- Configuring the ISDN LAN Modem from a Remote Location
- Supplementary Voice Call Services
- Placing, Receiving and Disconnecting Calls
- Troubleshooting and Maintenance
- Networking Primer
- What is a network?
- What is a LAN?
- What is a WAN?
- How does a LAN connect to a WAN?
- What is a LAN modem?
- What is ISDN?
- How do different devices communicate with each other?
- What is TCP/IP?
- What is an IP Address?
- What is a Subnet Mask?
- Dynamic and Static IP Addresses
- What is DHCP?
- What is DNS?
- What is NAT?
- What are numbered and unnumbered links?
- How is overall throughput determined?
- What is a network?
- Using the Custom Web Browser
- ISDN LAN Modem Factory Defaults
- ISDN LAN Modem Specifications
- Ordering ISDN Service
- If You Place Your ISDN Order Through 3Com
- If You Place Your ISDN Order Through the Telephone Company
- Supplementary Voice Features Included with U, EZ-ISDN-1, V and EZ-ISDN 1A
- Limitations of ISDN Ordering Codes U, EZ-ISDN 1, V and EZ-ISDN 1A
- What If I Already Have ISDN Service?
- Table of ISDN Ordering Code Capabilities
- Glossary
- Index
- 3Com Corporation Limited Warranty
Understanding VPNs and PPTP 23
Understanding VPNs
and PPTP
Virtual private networks (VPN) are private, secure networks created in public
networks such as the Internet. A VPN is essentially a secure, private tunnel within
the Internet. Since VPN calls are placed through a local ISP, they eliminate long
distance charges that would occur from directly dialing to a remote private
network.
One of the protocols which enables a VPN to be created is PPTP. The PPTP protocol
allows for multiple workstations to establish a secure multi-protocol connection to
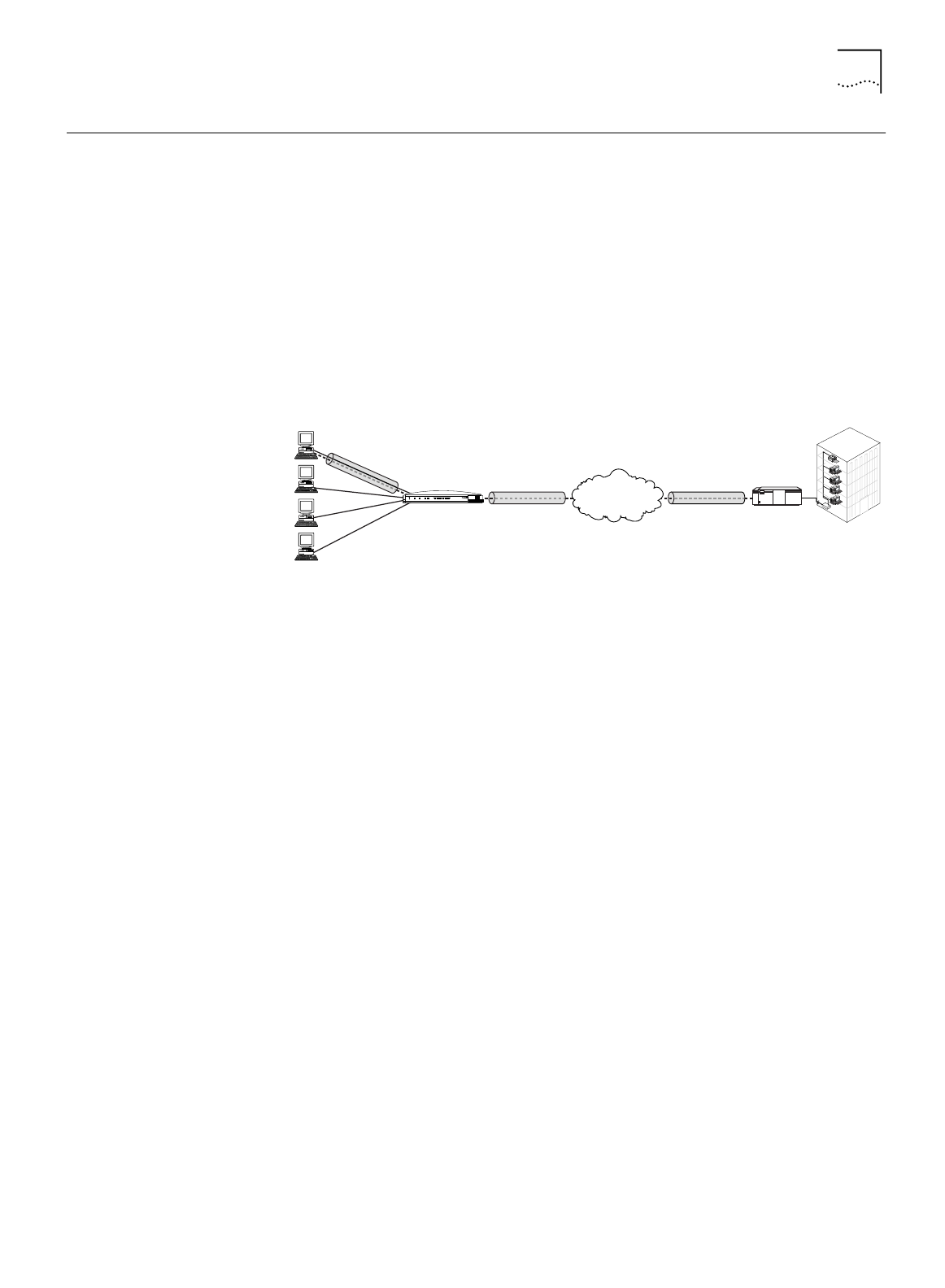
a remote, private network via a single, locally-dialed ISP account as shown in
Figure 10. Any networking protocols such as IP, IPX and NetBEUI can be supported
transparently through the tunnel. While the ISDN LAN Modem supports PPTP, it
does not play an active role in creating or terminating a tunnel.
Figure 10
Connection to an Remote Private Network via an ISP
The main steps for creating a VPN are as follows. Each step is explained in detail in
subsequent sections.
■ Set up the server side of the tunnel connection
■ Set up the client side of the tunnel connection
■ Initiate a tunnel between client and server using your client software
Setting Up the Server
Side of the Tunnel
In order to establish a tunnel, the client side must be able to dial into a PPTP tunnel
server on the remote private network such as 3Com’s NETBuilder, PathBuilder, and
Total Control Hub as well as Microsoft’s Windows NT server version 4.0 or later. If
you use Windows NT 4.0, then Service Pack 3 or greater and RAS must be
installed. Also, the protocols required for the private network must be installed on
the PPTP tunnel server. It is recommended that an experienced network
administrator set up the server side. Note that protocols required for the private
network must be installed on each PPTP tunnel client as well as the PPTP tunnel
server.
Setting Up the Client
Side of the Tunnel
In order to establish a tunnel, the client side must have PPTP tunnel client software
such as Windows Dial-Up Networking version 1.2 or higher which includes the
required software VPN adapter or Windows NT operating system with Service Pack
3, or Network TeleSystem’s TunnelBuilder™ VPN software for Windows 3.11 and
Macintosh operating systems. This software should reside on all workstations that
wish to create a tunnel to the tunnel server. Follow instructions provided for
installation and set up.
From the Edge to the Heart
of the Network.
3
C
om
POWER
ISDN
Alert
B1
B2 TX COLL 1 2 3 4
3 Com
LAN STATUS
ISDN LAN Modem
3C892
OK
Internet Service
Provider
LAN Modem
Tunnel
terminator
Corporate
network










