User Manual
Table Of Contents
- Contents
- Figures
- Preface
- Section I
- Basic Operations
- Chapter 1
- Starting a Web Browser Management Session
- Chapter 2
- Basic Switch Parameters
- Chapter 3
- Enhanced Stacking
- Chapter 4
- SNMPv1 and SNMPv2c Community Strings
- Chapter 5
- Port Parameters
- Chapter 6
- MAC Address Table
- Chapter 7
- Static Port Trunks
- Chapter 8
- Port Mirroring
- Section II
- Advanced Operations
- Chapter 9
- File System
- Chapter 10
- File Downloads and Uploads
- Chapter 11
- Event Log and Syslog Servers
- Chapter 12
- Classifiers
- Chapter 13
- Access Control Lists
- Chapter 14
- Quality of Service
- Chapter 15
- Class of Service
- Chapter 16
- IGMP Snooping
- Chapter 17
- Denial of Service Defense
- Chapter 18
- Power Over Ethernet
- Section III
- SNMPv3 Operations
- Chapter 19
- SNMPv3
- Enabling the SNMP Protocol
- Configuring the SNMPv3 User Table
- Configuring the SNMPv3 View Table
- Configuring the SNMPv3 Access Table
- Configuring the SNMPv3 SecurityToGroup Table
- Configuring the SNMPv3 Notify Table
- Configuring the SNMPv3 Target Address Table
- Configuring the SNMPv3 Target Parameters Table
- Configuring the SNMPv3 Community Table
- Displaying SNMPv3 Tables
- Section IV
- Spanning Tree Protocols
- Chapter 20
- Spanning Tree, Rapid Spanning Tree, and Multiple Spanning Tree Protocols
- Section V
- Virtual LANs
- Chapter 21
- Port-based and Tagged Virtual LANs
- Chapter 22
- GARP VLAN Registration Protocol
- Chapter 23
- Protected Ports VLANs
- Section VI
- Port Security
- Chapter 24
- MAC Address-based Port Security
- Chapter 25
- 802.1x Port-based Network Access Control
- Section VII
- Management Security
- Chapter 26
- Encryption Keys, PKI, and SSL
- Chapter 27
- Secure Shell Protocol
- Chapter 28
- TACACS+ and RADIUS Authentication Protocols
- Chapter 29
- Management Access Control List
- Index
Chapter 20: Spanning Tree, Rapid Spanning Tree, and Multiple Spanning Tree Protocols
276 Section IV: Spanning Tree Protocols
this aging time to test the age of stored configuration messages called
bridge protocol data units (BPDUs). For example, if you use the default
value 20, all bridges delete current configuration messages after 20
seconds. This parameter can be from 6 to 40 seconds.
In selecting a value for maximum age, the following rules must be
observed:
MaxAge must be greater than (2 x (HelloTime + 1))
MaxAge must be less than (2 x (ForwardingDelay - 1))
Note
The aging time for BPDUs is different from the aging time used by
the MAC address table.
Bridge Identifier
The MAC address of the bridge. The bridge identifier is used as a tie
breaker in the selection of the root bridge when two or more bridges
have the same bridge priority value. This value cannot be changed.
3. When you are finished setting the parameters, click Apply.
4. To adjust a port’s STP settings, click on the port in the switch image
and click Modify. You can select more than one port at a time.
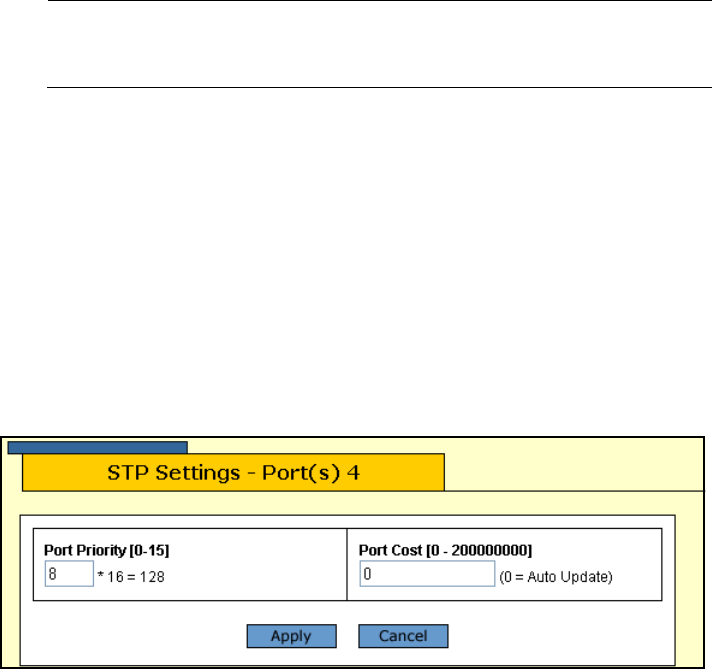
The STP Port Settings window is shown in Figure 93.
Figure 93. STP Port Settings Window
5. Adjust the settings as desired. The parameters are described below.
1 - Port Priority
This parameter is used as a tie breaker when two or more ports are
determined to have equal costs to the root bridge. The range for port
priority is 0 to 240. As with bridge priority, this range is broken into
increments, in this case multiples of 16. To select a port priority for a
port, you enter the increment of the desired value. Table 8 on
page 277 lists the values and increments. The default value is 128,
which is increment 8.










