User Manual
Table Of Contents
- Contents
- Figures
- Preface
- Section I
- Basic Operations
- Chapter 1
- Starting a Web Browser Management Session
- Chapter 2
- Basic Switch Parameters
- Chapter 3
- Enhanced Stacking
- Chapter 4
- SNMPv1 and SNMPv2c Community Strings
- Chapter 5
- Port Parameters
- Chapter 6
- MAC Address Table
- Chapter 7
- Static Port Trunks
- Chapter 8
- Port Mirroring
- Section II
- Advanced Operations
- Chapter 9
- File System
- Chapter 10
- File Downloads and Uploads
- Chapter 11
- Event Log and Syslog Servers
- Chapter 12
- Classifiers
- Chapter 13
- Access Control Lists
- Chapter 14
- Quality of Service
- Chapter 15
- Class of Service
- Chapter 16
- IGMP Snooping
- Chapter 17
- Denial of Service Defense
- Chapter 18
- Power Over Ethernet
- Section III
- SNMPv3 Operations
- Chapter 19
- SNMPv3
- Enabling the SNMP Protocol
- Configuring the SNMPv3 User Table
- Configuring the SNMPv3 View Table
- Configuring the SNMPv3 Access Table
- Configuring the SNMPv3 SecurityToGroup Table
- Configuring the SNMPv3 Notify Table
- Configuring the SNMPv3 Target Address Table
- Configuring the SNMPv3 Target Parameters Table
- Configuring the SNMPv3 Community Table
- Displaying SNMPv3 Tables
- Section IV
- Spanning Tree Protocols
- Chapter 20
- Spanning Tree, Rapid Spanning Tree, and Multiple Spanning Tree Protocols
- Section V
- Virtual LANs
- Chapter 21
- Port-based and Tagged Virtual LANs
- Chapter 22
- GARP VLAN Registration Protocol
- Chapter 23
- Protected Ports VLANs
- Section VI
- Port Security
- Chapter 24
- MAC Address-based Port Security
- Chapter 25
- 802.1x Port-based Network Access Control
- Section VII
- Management Security
- Chapter 26
- Encryption Keys, PKI, and SSL
- Chapter 27
- Secure Shell Protocol
- Chapter 28
- TACACS+ and RADIUS Authentication Protocols
- Chapter 29
- Management Access Control List
- Index
AT-S62 Management Software Web Browser Interface User’s Guide
Section VI: Port Security 325
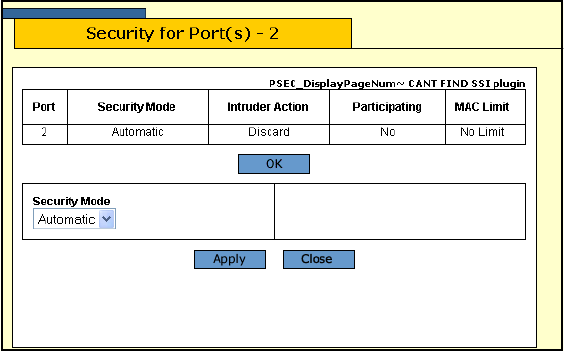
The Security for Port(s) window is shown in Figure 106.
Figure 106. Security for Port(s) Window
The top portion of the window displays the current security settings of
the selected ports.
6. From the Security Mode pull-down menu, select the desired port
security level for the port. Options are:
Automatic
Disables port security on a port. This is the default setting.
Limited
Allows you to specify a maximum number of dynamic source MAC
addresses a port can learn. Once a port has learned its maximum
number, it will not learn any new addresses and will only accept frames
from the source nodes of the learned addresses.
A dynamic MAC address learned on a port operating in the Limited
security mode never times out from the MAC address table, even
when the corresponding end node is inactive.
You can add static addresses to a port running this security level. Static
addresses are not included in the count of the maximum number of
dynamic addresses.
Secured
Instructs a port to forward frames using only static MAC address. The
port will not learn any dynamic MAC addresses and will delete any
dynamic addressees that it has already learned. Only those end nodes
whose MAC addresses are entered as static addresses can forward
frames through the port.
Locked
Instructs a port to immediately stop learning new dynamic MAC
addresses. Frames are forwarded using the dynamic MAC addresses










