User guide
Table Of Contents
- Contents
- Figures
- Tables
- Preface
- Section I
- Basic Operations
- Chapter 1
- Basic Switch Parameters
- Configuring the Switch’s Name, Location, and Contact
- Changing the Manager and Operator Passwords
- Setting the System Date and Time
- Rebooting a Switch
- Pinging a Remote System
- Returning the AT-S63 Management Software to the Factory Default Values
- Displaying the IP Address of the Local Interface
- Displaying System Information
- Chapter 2
- Port Parameters
- Chapter 3
- Enhanced Stacking
- Chapter 4
- SNMPv1 and SNMPv2c
- Chapter 5
- MAC Address Table
- Chapter 6
- Static Port Trunks
- Chapter 7
- Port Mirroring
- Section II
- Advanced Operations
- Chapter 8
- File System
- Chapter 9
- File Downloads and Uploads
- Chapter 10
- Event Logs and Syslog Client
- Chapter 11
- Classifiers
- Chapter 12
- Access Control Lists
- Chapter 13
- Class of Service
- Chapter 14
- Quality of Service
- Chapter 15
- Denial of Service Defenses
- Chapter 16
- IGMP Snooping
- Section III
- SNMPv3
- Chapter 17
- SNMPv3
- Configuring the SNMPv3 Protocol
- Enabling or Disabling SNMP Management
- Configuring the SNMPv3 User Table
- Configuring the SNMPv3 View Table
- Configuring the SNMPv3 Access Table
- Configuring the SNMPv3 SecurityToGroup Table
- Configuring the SNMPv3 Notify Table
- Configuring the SNMPv3 Target Address Table
- Configuring the SNMPv3 Target Parameters Table
- Configuring the SNMPv3 Community Table
- Displaying SNMPv3 Tables
- Section IV
- Spanning Tree Protocols
- Chapter 18
- Spanning Tree and Rapid Spanning Tree Protocols
- Chapter 19
- Multiple Spanning Tree Protocol
- Section V
- Virtual LANs
- Chapter 20
- Port-based and Tagged VLANs
- Chapter 21
- GARP VLAN Registration Protocol
- Section VI
- Port Security
- Chapter 22
- MAC Address-based Port Security
- Chapter 23
- 802.1x Port-based Network Access Control
- Section VII
- Management Security
- Chapter 24
- Encryption Keys, PKI, and SSL
- Chapter 25
- Secure Shell (SSH)
- Chapter 26
- TACACS+ and RADIUS Protocols
- Chapter 27
- Management Access Control List
- Index
AT-S63 Management Software Web Browser User’s Guide
Section II: Advanced Operations 127
Modifying the
Event Log Full
Action
This procedure controls the action of an event log after reaching its
maximum capacity of events. There are two possible actions. In the first
action a log deletes the oldest entries as it adds new entries. In the second
action the log stops adding entries to preserve the log contents.
Note
The switch continues to send events to syslog servers even when
the logs are full.
To configure the event log full action, do the following procedure:
1. From the home page, select Configuration.
2. From the Configuration menu, select the System option.
3. Select the Event Log tab.
The Event log tab is shown in Figure 33 on page 121.
4. Under Current Log Outputs, select Output 0, Permanent, to configure
the log in permanent memory, or Output 1, Temporary, to configure the
log in temporary memory.
5. Click Modify.
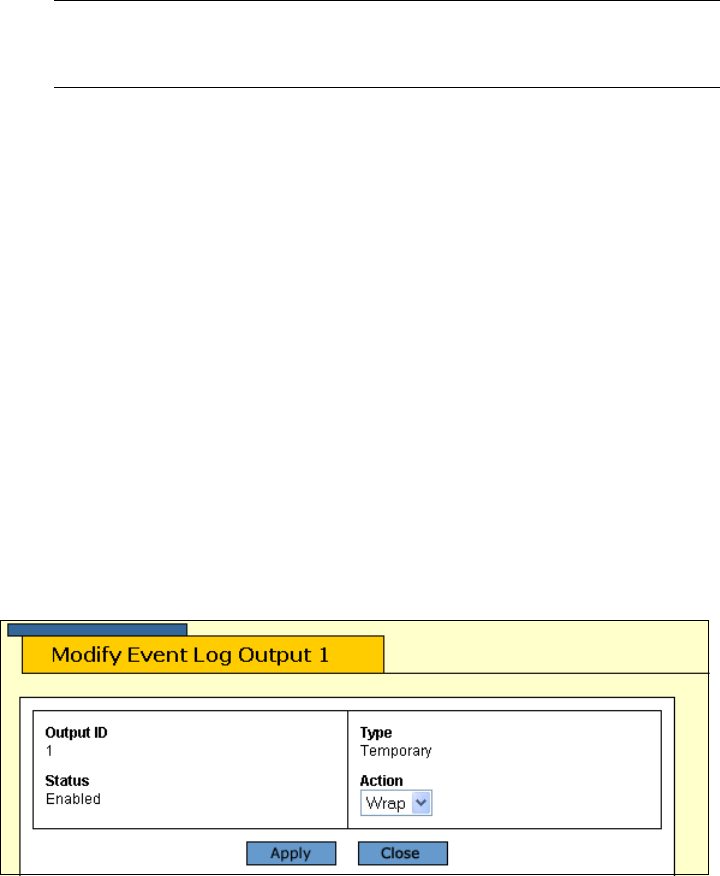
The Modify Event Log Output window is displayed. The window for the
temporary memory log is shown in Figure 36.
Figure 36. Modifying Event Log Output 1 Window
6. Using the Action pull-down menu, select one of the following:
Wrap
The log deletes the oldest entries as it adds new entries after reaching
its maximum storage capacity.
Halt
The log stops adding new entries to preserve the contents of the log.










