Technical information
Large Business Communications Systems
4-4 Issue 7 June 2001
*For ASAI, see the applicable product feature description.
Barrier Codes
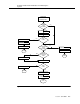
Figure 4-1 illustrates how barrier codes and/or authorization codes can provide
added security for Remote Access calls. Refer to this flowchart as necessary
throughout the sections on Barrier Codes and Authorization Codes.
Table 4-1. Security Tools for Remote Access
Security Tool Switch Page #
Barrier Code All 4-4
Authorization Code DEFINITY ECS,
DEFINITY G1, G2, G3,
System 85, and
System 75 (R1V3)
4-7
Feature Access Code
Administration
All 4-8
Trunk Administration All 4-8
Remote Access Dial Tone DEFINITY ECS,
DEFINITY G1, G2, G3,
System 85, and
System 75 (R1V3)
4-8
Night Service All 4-9
Call Vectoring DEFINITY ECS and
DEFINITY G3
4-9
Call Prompting/ASAI* DEFINITY ECS and
DEFINITY G2 and G3
4-10
Barrier Code Aging/Access
Limits
DEFINITY G3V3 and
later including
DEFINITY ECS
4-66
Security Violation Notification
(SVN)
DEFINITY ECS and
DEFINITY G3
4-57
Status Remote Access
Command
DEFINITY G3V4 and
later including
DEFINITY ECS
4-11
Logoff Screen Enhancements DEFINITY G3V4 and
later including
DEFINITY ECS
4-11