Avid MediaCentral Platform Services ® Security Architecture and Analysis Purpose of This Document This document provides the MediaCentral administrator with an overview of the security architecture for the MediaCentral environment and recommended best practices for a secure operation. The document also provides an analysis of the MediaCentral UX application against the most common security flaws for Web-based applications.
Revision History Date Revised Changes Made November 23, 2015 Added multiple-zone port information. See “MediaCentral Security Architecture” on page 6. Updated version to MediaCentral version 2.4. July 13, 2015 June 27, 2014 First publication of version 2.3. • Added information about strong password validation. See “User Authentication” on page 8. • Added information for Media Index. See “Media Index Security” on page 16 Version 2.0 published. Contents Overview of MediaCentral . . . . . . . . . .
Overview of MediaCentral Overview of MediaCentral MediaCentral Platform Services deliver workflow tools for media professionals through both Web and mobile applications. The MediaCentral UX application allows individuals in different media production roles to access the tools they need to complete tasks with greater access to assets, team collaboration, and workflow agility. Through MediaCentral UX, users can access existing Interplay Production assets and iNEWS story/rundown information.
Overview of MediaCentral Security In order to provide for a single login experience, MediaCentral stores user login credentials (MediaCentral, iNEWS, Interplay Production, and other customer user account information) in a central user management database. All data is stored in this central database and all passwords are maintained in an encrypted form. Note that MediaCentral leverages the existing iNEWS and Interplay Production credentials (no modifications are made to existing accounts).
Overview of MediaCentral Security Disaster Recovery and Business Continuity • The MediaCentral application can operate within a clustered server configuration, providing Active/Passive failover for continuity of services. • The MediaCentral Playback Services (MCPS), which supports the player functionality in the MediaCentral UI, is also load balanced, providing performance and failover support for video streaming.
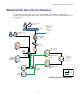
MediaCentral Security Architecture MediaCentral Security Architecture The diagram below provides an overview of the MediaCentral architecture with specific references to application and data security. This diagram shows a clustered MediaCentral server configuration.
MediaCentral Security Architecture A MediaCentral client requires user login credentials in order to gain access to the underlying functionality. All data transfer to and from the MediaCentral client (user credentials, session information, user configuration settings, media images and files, text, and machine instructions) are transported in a secure manner to the MediaCentral server using HTTPS protocol.
MediaCentral Security Architecture n Outbound ACLs should be used to allow packets from the MediaCentral server to the MediaCentral client over “established” TCP sessions only. The “established” keyword indicates that packets belong to an existing connection if the TCP datagram has the Acknowledgment (ACK) or Reset (RST) bit set. In addition to the ports listed above, Multi-Zone and Media Index configurations require additional ports to enable communication between the zones.
MediaCentral Security Architecture User passwords created in MediaCentral UX v2.1 and later require strong password validation: n • Minimum length of user names: 1 character • Minimum length of passwords: 6 characters • Maximum length of user names and passwords: 255 characters • Passwords are case-sensitive. • Passwords cannot contain all or part of the user’s account name. • Passwords cannot consist of spaces only.
MediaCentral Security Architecture MediaCentral queries the User Management Service to determine which MediaCentral layouts are to be made available to the user upon login. Access to all assets (media, metadata, rundowns, stories) is managed by the backend systems themselves (Interplay Production, iNEWS). The MediaCentral User Management Service authorizes all client requests against the privileges for the current session.
MediaCentral Security Architecture Security Data in Transit MediaCentral uses default HTTPS transfer from the Web client to the MediaCentral server and all underlying MediaCentral services (for example, User Management). HTTPS calls are sent over port 443; see Table 1 on page 7 on for a complete list of ports. Note that a network firewall is recommended for all configurations. Communication between MediaCentral and Interplay Production and iNEWS is sent over the house network in an unsecured fashion.
MediaCentral Security Architecture MediaCentral v2.0 and later allows search and delivery of assets through a multi-zone configuration. By default, a MediaCentral system is configured as a single zone. Large organizations can combine two or more single-zone systems into a multi-zone environment. Multi-zone functionality is designed for deployment across an internal secure network (“corporate network”) with all traffic occurring behind the firewall.
MediaCentral Security Architecture Table 4: Security Implications for Certificate Types No Certificate Self-Signed Commercially Issued User experience User is prompted with “This site is untrusted” with options to back out or “Proceed Anyway.” User is prompted with Login is transparent. “This site is untrusted” with options to back out or “Proceed Anyway.” Login is transparent.
Strategies and Best Practices Strategies and Best Practices Administrator Accounts As part of the MediaCentral installation process, default administrator accounts are created. After a successful installation, these account passwords must be updated. • A default operating system account is created on the MediaCentral server using the following credentials: user: root password: Avid123 Note that each cluster node will have a similar account.
Strategies and Best Practices Port Settings The following table lists the ports that are required by the MediaCentral server. Check with your Avid representative for the exact configuration. For ports used by Media Index, see “Media Index Server Ports” on page 18.
Media Index Security Media Index Security Media Index Overview Media Index delivers an API for fast and efficient search across multiple data sources, including Interplay Production, iNEWS, and Media Archive. It also provides an integration point for third-party systems. Media Index, in conjunction with MediaCentral, allows users to search metadata and access assets transparently, regardless of the data source and physical asset location.
Media Index Security Disaster Recovery and Business Continuity Media Index can operate within a clustered environment, providing Active/Active failover. High availability of the Media Index API is provided by Pacemaker. Elasticsearch as an underlying data storage provides continuous data replication and high availability. Media Index Architecture Media Index is delivered with the MediaCentral installer and operates on the MediaCentral servers.
Media Index Security Media Index Server Ports The Media Index API is exposed through ACS bus technology. A client accesses the Media Index API through the MediaCentral middleware and ACS bus. The following table lists the ports used Table 6: Media Index Server Ports Component Port Protocol Usage Elasticsearch 9200 HTTP Elasticsearch HTTP calls 9300 TCP Internal Elasticsearch node to node communication 9201 HTTP Elasticsearch-tribe HTTP calls.
Security Risk Assessment Security Risk Assessment The following table describes how MediaCentral addresses security risks as described in the Open Web Application Security Project (OWASP). Each threat is a link to the corresponding section of the project Web site, available at https://www.owasp.org/index.php/Top_10_2010-Main.
Security Risk Assessment Table 7: Security Risk Assessment Threat Risk Typical Security Measures MediaCentral Environment Cross Site Request Legitimizes forged Unique session or Forgery browser requests request tokens Impact MediaCentral uses unique user session Low tokens. All tokens are deleted upon session exit. Session IDs are mapped to specific machines.
Security Risk Assessment Table 7: Security Risk Assessment Threat Risk Insufficient Transport Layer Protection Unprotected network traffic Typical Security Measures MediaCentral Environment SSL authentications MediaCentral configuration utilizes SSL transport protocol and VPN VPN network access. Backend SSL All access requests to the transport MediaCentral database requires a Secure database suitable username and password.
Where to Find More Information Where to Find More Information MediaCentral documentation can be found on the Avid Customer Support Knowledge Base. Version 2.3 documentation is located here: http://avid.force.com/pkb/articles/en_US/ReadMe/Avid-MediaCentral-Version-2-3-x-Document ation Legal Notices Copyright © 2015 Avid Technology, Inc. and its licensors. All rights reserved. Attn. Government User(s). Restricted Rights Legend U.S. GOVERNMENT RESTRICTED RIGHTS.