User's Manual Part 4
Dual-Band Wireless A+G Broadband Router
4544
L2TP - Layer Two Tunneling Protocol is an extension of the Point-to-Point
Tunneling Protocol (PPTP) used by to enable the operation of a virtual pri-
vate network (VPN) over the Internet.
PPTP - Point-to-Point Tunneling Protocol is the method used to enable
VPN sessions to a Windows NT 4.0 or 2000 server. To allow PPTP tunnels
to pass through the Router, PPTP Pass-Through is enabled by default. To
disable PPTP Pass-Through, uncheck the box next to PPTP.
Web Filters Using the Web Filters feature, you may enable up to four specif-
ic filtering methods.
Proxy - Use of WAN proxy servers may compromise the Router's security.
Denying Proxy will disable access to any WAN proxy servers. To enable
proxy filtering, click the Proxy box.
Java - Java is a programming language for websites. If you deny Java, you
run the risk of not having access to Internet sites created using this pro-
gramming language. To enable Java filtering, click the Java box.
ActiveX - ActiveX is a programming language for websites. If you deny
ActiveX, you run the risk of not having access to Internet sites created using
this programming language. To enable ActiveX filtering, click the ActiveX
box.
Figure 7-12
Instant Wireless
®
Series
Passphrase Instead of manually entering WEP keys, you can enter a
Passphrase. This Passphrase is used to generate one or more WEP keys. It is
case-sensitive and should not be longer than 16 alphanumeric characters. This
Passphrase function is compatible with Linksys wireless products only. [If you
want to communicate with non-Linksys wireless products, enter the WEP
key(s) manually on the non-Linksys wireless products.] After you enter the
Passphrase, click the Generate button to create WEP keys.
Keys 1-4 WEP keys enable you to create an encryption scheme for wireless
LAN transmissions. Manually enter a set of values. (Do not leave a key field
blank, and do not enter all zeroes. These are not valid key values.) Keys 1-4
offer 64-bit or 128-bit encryption.
If you are using 64-bit WEP encryption, then the key must be exactly 10 hexa-
decimal characters in length. If you are using 128-bit WEP encryption, then the
key must be exactly 26 hexadecimal characters in length. Valid hexadecimal
characters are “0”-“9” and “A”-“F”.
Check all the values, and click theApply button to save your 2.4GHz, Wireless-
G WEP settings.
To apply any of the settings you change on this page, click the Apply button.
To cancel any changes you’ve entered on this page, click the Cancel button. To
get more information about the features, click the Help button.
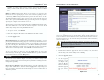
The Security screen, shown in Figure 7-12, allows you to change the Router’s
security settings. You should change the factory default password, which is
admin, to your own as soon as possible. All users who try to access the Router’s
web-based utility or Setup Wizard will be prompted for the Router’s password.
Router Password The new Password must not exceed 32 characters in length
and must not include any spaces. Enter the new Password in the second field to
confirm it.
VPN Pass-Through Virtual Private Networking (VPN) is typically used for
work-related networking. For VPN tunnels, the Router supports IPSec Pass-
Through and PPTP Pass-Through.
IPSec - Internet Protocol Security (IPSec) is a suite of protocols used to
implement secure exchange of packets at the IP layer. To allow IPSec tun-
nels to pass through the Router, IPSec Pass-Through is enabled by default.
To disable IPSec Pass-Through, uncheck the box next to IPSec.
Security