API Guide
NOTE: Option 82 is supported, but not configurable.
DHCP snooping
DHCP snooping is a layer 2 security feature that helps networking devices to monitor DHCP messages and block untrusted or
rogue DHCP servers.
When you enable DHCP snooping on a switch, it begins monitoring transactions between trusted DHCP servers and DHCP
clients and uses the information to build the DHCP snooping binding table. You configure interfaces that connect to DHCP
servers as trusted interfaces. All other interfaces are untrusted by default.
The DHCP snooping binding table contains the following information:
● Client IP addresses
● Client MAC addresses
● Interface facing the clients
● Client VLAN
● Lease time
● DHCP binding type – static or dynamic
The switch considers DHCP servers connected to trusted interfaces on the switch as legitimate servers. When a switch
receives DHCP server-initiated packets (UDP destination port 67) on an untrusted interface, it drops the packet.
When a switch receives DHCP renew, release, or decline messages from a client, it checks the DHCP snooping binding table for
a match. If the information in the DHCP message matches the table, the switch forwards the message to the DHCP server. If
the information does not match, the switch interprets the client as an unauthorized client and drops the packet.
The DHCP snooping switch removes a dynamically-learned DHCP snooping binding entry when one of the following occurs:
● Lease expiry
● DHCP RELEASE packet received from the client
● DHCP DECLINE packet received from the client
● User actions, such as DHCP clear or disabling DHCP snooping
You can add a static DHCP snooping binding entry using the CLI. If you add a static entry for a client, any dynamic entry that is
present for the same client is overwritten. The switch does not remove static entries if it receives DHCP RELEASE or DHCP
DECLINE packets.
By default, DHCP snooping is disabled globally and enabled on VLANs. For the DHCP snooping feature to work, enable it
globally.
NOTE:
If you move a DHCP client from an untrusted interface to another untrusted interface within the VLAN, the DHCP
snooping binding database is not updated. The switch drops subsequent packets from the client. However, if you move a
DHCP client from an untrusted interface to a trusted interface, there is no impact to the traffic from the client.
Restrictions for DHCP snooping
● The management VLAN does not support DHCP snooping.
● VxLAN bridges do not support DHCP snooping.
● The maximum number of supported DHCP snooping binding entries is 4000.
● OS10 does not support multi-hop DHCP snooping.
● For the DHCP snooping functionality to work correctly, ensure that the DHCP server supports option 82 (RFC 3046).
● Enable option 82 (RFC 3046) on the DHCP server for the DHCP Snooping functionality to work correctly.
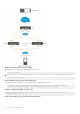
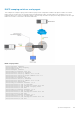
Rogue DHCP server detection
In the following topology, a trusted DHCP server, a DHCP client, and a rogue DHCP server are connected to the DHCP
snooping switch. The DHCP client and DHCP server are on the same VLAN. The physical interface eth 1/1/2 is a trusted
interface. When the rogue DHCP server sends a DHCP packet to the client, the switch analyzes the packet. As the rogue server
is connected to the switch to an untrusted eth 1/1/3 interface the switch deems the server as a rogue DHCP server and drops
the packet.
System management
211