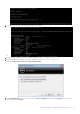
Administrator Guide
Table Of Contents
- Encryption Recovery v11.1
- Contents
- Getting Started with Recovery
- Policy-Based or File/Folder Encryption Recovery
- Hardware Crypto Accelerator Recovery
- Self-Encrypting Drive (SED) Recovery
- Full Disk Encryption Recovery
- Full Disk Encryption and Dell Encryption Recovery
- PBA Device Control
- General Purpose Key Recovery
- BitLocker Manager Recovery
- Password Recovery
- Encryption External Media Password Recovery
- Appendix A - Download the Recovery Environment
- Appendix B - Creating Bootable Media
PBA Device Control
PBA Device Control applies to endpoints encrypted with SED or Full Disk Encryption.
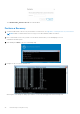
Use PBA Device Control
PBA commands for a specific endpoint are carried out in the PBA Device Control area. Each command has a priority ranking.
A command with a higher priority rank cancels commands of lower priorities in the enforcement queue. For a list of command
priority rankings, see AdminHelp available by clicking the ? in the Remote Management Console. The PBA Device Controls are
available on the Endpoint Details page of the Remote Management Console.
The following commands are available in PBA Device Control:
● Lock - Locks the PBA screen and prevents any user from logging into the computer.
● Unlock - Unlocks the PBA screen after it has been locked on this endpoint, either by sending a Lock command or by
exceeding the maximum number of authentications attempts allowed by policy.
●
Remove Users - Removes all users from the PBA.
● Bypass Login - Bypasses the PBA screen one time to allow a user into the computer without authenticating. The user will
still need to login to Windows after PBA has been bypassed.
● Wipe - The Wipe command functions as a “restore to factory state” for the encrypted drive. The Wipe command can
be used to re-purpose a computer or, in an emergency situation, wipe the computer, making the data permanently
unrecoverable. Ensure that this is the desired behavior before invoking this command. For Full Disk Encryption, the Wipe
command cryptographically erases the drive and the PBA is removed. For SED, the Wipe command cryptographically erases
the drive and the PBA displays "Device Locked". To re-purpose the SED, remove the PBA with the SED Recovery app.
7
46 PBA Device Control