Setup Guide
Table Of Contents
- 1 Introduction
- 2 iDRAC9 Configuration for RSA SecurID
- 3 RSA SecurID 2FA with Local Users
- 4 RSA SecurID 2FA with Active Directory Users
- 5 RSA SecurID 2FA with Generic LDAP Directory Users
- 6 Troubleshooting RSA SecurID Issues
- 6.1 Misconfiguration or iDRAC Configuration Gets Reset
- 6.2 Datacenter License Expires or Gets Downgraded or Deleted
- 6.3 Authentication Failures without being Prompted for RSA Passcode
- 6.4 Authentication failures with Correct RSA Passcode
- 6.5 Authentication Failures with Correct RSA Passcode due to Timeout
- 6.6 RSA Configuration gets lost after importing Server Configuration Profile
- Appendix A: Configure iDRAC Using RACADM
- Appendix B: References
iDRAC9 Configuration for RSA SecurID
ID 450
2 iDRAC9 Configuration for RSA SecurID
iDRAC9 can only be configured to authenticate with a single RSA AM server at a time. These global settings
on RSA AM server apply to all iDRAC local users, AD and LDAP users. We will go through each in details in
the following sections:
2.1 RSA SecurID 2FA Global Configuration
To enable RSA SecureID on iDRAC, the following attributes from the RSA AM server are required:
RSA Authentication API URL
RSA Client-ID
RSA Access Key
RSA AM server certificate (chain)
RSA Authentication API URL
The URL syntax is: https://<rsa-am-server-hostname>:<port>/mfa/v1_1, and by default the port is 5555.
RSA Client ID
By default, the RSA client ID is the same as the RSA AM server hostname. Find the RSA client ID at RSA AM
server's authentication agent configuration page.
RSA Access Key
The Access Key can be retreived on RSA AM by navigating to Setup -> System Settings -> RSA SecurID
Authentication API section, which is usually displayed as
“l98cv5x195fdi86u43jw0q069byt0x37umlfwxc2gnp4s0xk11ve2lffum4s8302”.
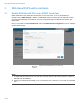
To configure the setting through iDRAC GUI,
1. Go to iDRAC Settings -> Users.
2. From “Local Users” section, select an existing local user and click Edit button.
3. Scroll down to the bottom at the configuration page.
4. In the RSA SecurID section, follow the link of RSA SecurID Configuration to view or edit these
settings.
Another option,
1. Navigate from iDRAC Settings -> Users.
2. From “Directory Services” section, select Microsoft Active Service or Generic LDAP Directory
Service, and click the Edit button.
3. You will find the same link to configure these global settings, and that is covered in a later section of
this paper.
The figure below shows what this configuration page looks like.