User manual
Table Of Contents
- Zynq-7000 All Programmable SoC
- Table of Contents
- Ch. 1: Introduction
- Ch. 2: Signals, Interfaces, and Pins
- Ch. 3: Application Processing Unit
- Ch. 4: System Addresses
- Ch. 5: Interconnect
- Ch. 6: Boot and Configuration
- Ch. 7: Interrupts
- Ch. 8: Timers
- Ch. 9: DMA Controller
- Introduction
- Functional Description
- DMA Transfers on the AXI Interconnect
- AXI Transaction Considerations
- DMA Manager
- Multi-channel Data FIFO (MFIFO)
- Memory-to-Memory Transfers
- PL Peripheral AXI Transactions
- PL Peripheral Request Interface
- PL Peripheral - Length Managed by PL Peripheral
- PL Peripheral - Length Managed by DMAC
- Events and Interrupts
- Aborts
- Security
- IP Configuration Options
- Programming Guide for DMA Controller
- Programming Guide for DMA Engine
- Programming Restrictions
- System Functions
- I/O Interface
- Ch. 10: DDR Memory Controller
- Introduction
- AXI Memory Port Interface (DDRI)
- DDR Core and Transaction Scheduler (DDRC)
- DDRC Arbitration
- Controller PHY (DDRP)
- Initialization and Calibration
- DDR Clock Initialization
- DDR IOB Impedance Calibration
- DDR IOB Configuration
- DDR Controller Register Programming
- DRAM Reset and Initialization
- DRAM Input Impedance (ODT) Calibration
- DRAM Output Impedance (RON) Calibration
- DRAM Training
- Write Data Eye Adjustment
- Alternatives to Automatic DRAM Training
- DRAM Write Latency Restriction
- Register Overview
- Error Correction Code (ECC)
- Programming Model
- Ch. 11: Static Memory Controller
- Ch. 12: Quad-SPI Flash Controller
- Ch. 13: SD/SDIO Controller
- Ch. 14: General Purpose I/O (GPIO)
- Ch. 15: USB Host, Device, and OTG Controller
- Introduction
- Functional Description
- Programming Overview and Reference
- Device Mode Control
- Device Endpoint Data Structures
- Device Endpoint Packet Operational Model
- Device Endpoint Descriptor Reference
- Programming Guide for Device Controller
- Programming Guide for Device Endpoint Data Structures
- Host Mode Data Structures
- EHCI Implementation
- Host Data Structures Reference
- Programming Guide for Host Controller
- OTG Description and Reference
- System Functions
- I/O Interfaces
- Ch. 16: Gigabit Ethernet Controller
- Ch. 17: SPI Controller
- Ch. 18: CAN Controller
- Ch. 19: UART Controller
- Ch. 20: I2C Controller
- Ch. 21: Programmable Logic Description
- Ch. 22: Programmable Logic Design Guide
- Ch. 23: Programmable Logic Test and Debug
- Ch. 24: Power Management
- Ch. 25: Clocks
- Ch. 26: Reset System
- Ch. 27: JTAG and DAP Subsystem
- Ch. 28: System Test and Debug
- Ch. 29: On-Chip Memory (OCM)
- Ch. 30: XADC Interface
- Ch. 31: PCI Express
- Ch. 32: Device Secure Boot
- Appx. A: Additional Resources
- Appx. B: Register Details
- Overview
- Acronyms
- Module Summary
- AXI_HP Interface (AFI) (axi_hp)
- CAN Controller (can)
- DDR Memory Controller (ddrc)
- CoreSight Cross Trigger Interface (cti)
- Performance Monitor Unit (cortexa9_pmu)
- CoreSight Program Trace Macrocell (ptm)
- Debug Access Port (dap)
- CoreSight Embedded Trace Buffer (etb)
- PL Fabric Trace Monitor (ftm)
- CoreSight Trace Funnel (funnel)
- CoreSight Intstrumentation Trace Macrocell (itm)
- CoreSight Trace Packet Output (tpiu)
- Device Configuration Interface (devcfg)
- DMA Controller (dmac)
- Gigabit Ethernet Controller (GEM)
- General Purpose I/O (gpio)
- Interconnect QoS (qos301)
- NIC301 Address Region Control (nic301_addr_region_ctrl_registers)
- I2C Controller (IIC)
- L2 Cache (L2Cpl310)
- Application Processing Unit (mpcore)
- On-Chip Memory (ocm)
- Quad-SPI Flash Controller (qspi)
- SD Controller (sdio)
- System Level Control Registers (slcr)
- Static Memory Controller (pl353)
- SPI Controller (SPI)
- System Watchdog Timer (swdt)
- Triple Timer Counter (ttc)
- UART Controller (UART)
- USB Controller (usb)
Zynq-7000 AP SoC Technical Reference Manual www.xilinx.com 766
UG585 (v1.11) September 27, 2016
Chapter 32: Device Secure Boot
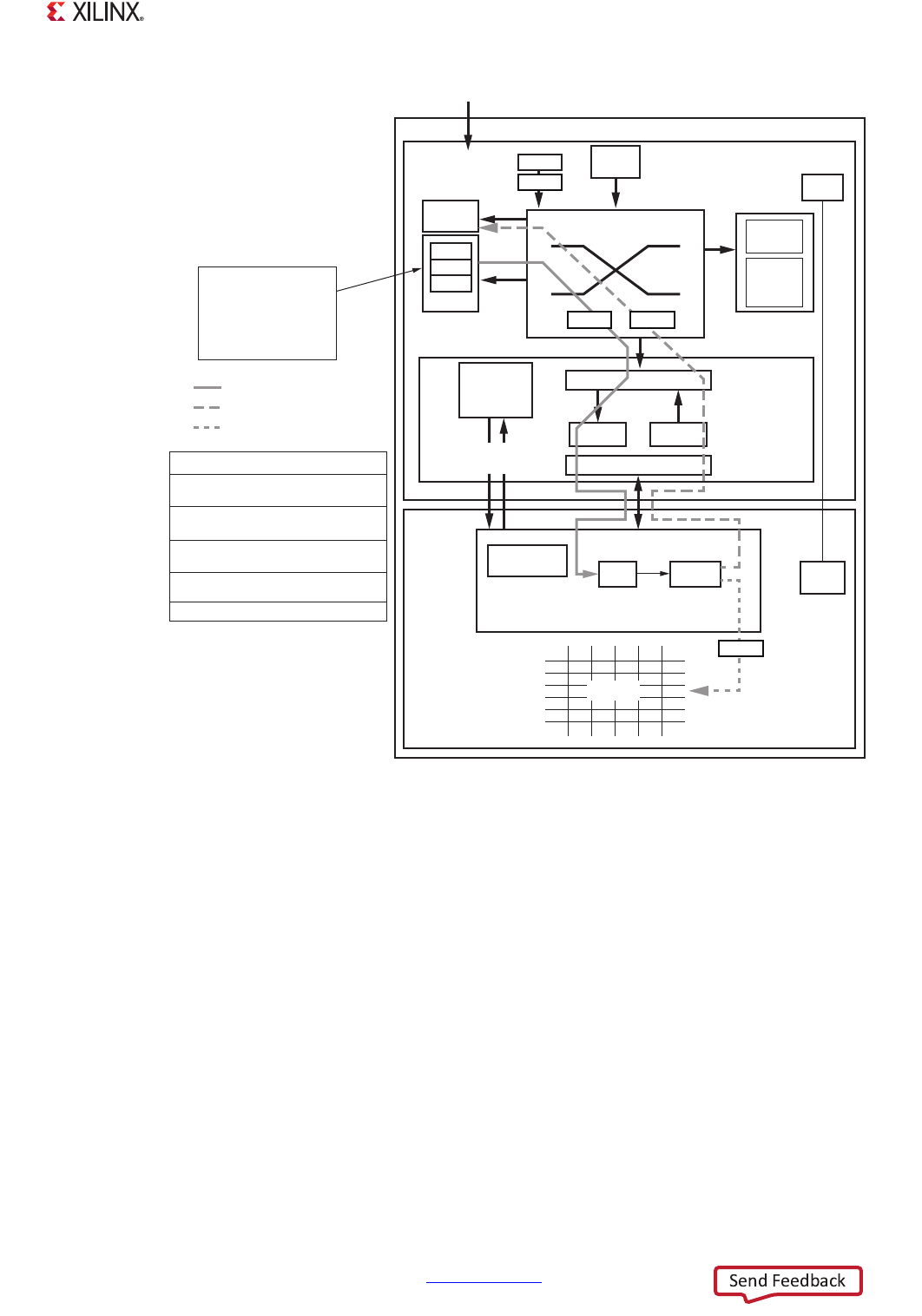
A device secure boot involves several systems contained within the AP SoC device. The secure boot
process is always initiated by the BootROM. If RSA authentication has been enabled the BootROM will
use the public key to authenticate the first stage boot loader (FSBL) before it is decrypted or executed.
If the boot image header indicates a secure boot, the BootROM enables the AES and HMAC engines
which reside in the PL. The encrypted FSBL is then sent by the BootROM to the AES and HMAC, a
hardened core within the PL, via the processor configuration access port (PCAP). The FSBL image is
decrypted and sent back to the PS via the PCAP where it is loaded into the on-chip RAM (OCM) for
execution. The PS is then able to securely configure the PL by sending an encrypted bitstream
through the PCAP to the AES/HMAC for decryption, authentication, and distribution to the PL
memory cells.
X-Ref Target - Figure 32-1
Figure 32-1: Secure Boot Block Diagram
CPU0
CPU1
AXI Top Switch
Configuration File 1
Secure FSBL
RSA authenticated,
AES encrypted
with SHA-256 HMAC)
NAND
NOR
QSPI
IOP
On-Chip
RAM
DDR
Memory
Controller
MDDR
FIFO
Secure
Vault
Processing System
Zynq-7000 AP SoC
Programmable Logic
Common Boot Path
PS Boot Path
PL Configuration Path
Step 1: Power applied, BootROM begins
execution
Step 2: (Optional) RSA authentication
performed on encrypted FSBL
Step 3: FSBL decryption (AES) and
authentication (HMAC)
Step 4: Decrypted, authenticated FSBL
stored in OCM
Step 5: (Optional) PL configuration
Secure Boot Process
JTAG
DAP
Device Key
AXI
FIFO
eFuse/BBRAM
Security
AES HMAC
PCAP
Device
Configuration
Block
ROM
Step 1
Mode_Mode MIO pins
PL
UG585_c33_01_052913
Step 3 Step 4
Step 5










