Wireless Modem Router User's Manual
Table Of Contents
- Version 2.4
- Before You Use
- Unpacking
- Features
- ADSL Compliance
- ADSL2 Compliance
- ADSL2+ Compliance
- Wireless LAN Compliance
- ATM Features
- Bridging Features
- Routing Features
- Security Features
- Configuration and Management
- Subscription for ADSL Service
- Notes and Cautions
- Chapter 1: Overview
- Physical Outlook
- Front Panel
- LED Indicators
- Rear Panel
- Chapter 2: System Requirement and Installation
- System Requirement
- Choosing a place for the ADSL Router
- Connecting the ADSL Router
- USB Driver Installation
- For Windows ME
- For Windows 2000
- For Windows XP
- For Windows Vista
- Uninstalling the USB Driver
- For Windows ME
- For Windows 2000
- For Windows XP
- For Windows Vista
- Setting up TCP/IP
- For Windows 98
- For Windows ME
- For Windows NT
- For Windows 2000
- For Windows XP
- For Windows Vista
- Renewing IP Address on Client PC
- For Windows 98/ME
- For Windows NT/2000/XP
- For Windows Vista
- Chapter 3: Accessing the Internet
- PPP over ATM (PPPoA) Mode
- Description:
- Configuration:
- PPP over ATM (PPPoA) IP Extension Mode
- Description:
- Configuration:
- PPP over Ethernet (PPPoE) Mode
- Description:
- Configuration:
- PPP over Ethernet (PPPoE) IP Extension Mode
- Description:
- Configuration:
- Numbered IP over ATM (IPoA)
- Description:
- Configuration:
- Numbered IP over ATM (IPoA)+NAT
- Description:
- Configuration:
- Unnumbered IP over ATM (IPoA)
- Description:
- Configuration:
- Unnumbered IP over ATM (IPoA)+NAT
- Description:
- Configuration:
- Bridge Mode
- Description:
- Configuration:
- MER
- Description:
- Configuration:
- Chapter 4: Web Configuration
- Using Web-Based Manager
- Outline of Web Manager
- To Have the New Settings Take Effect
- Language
- Quick Start
- Connect to Internet
- Quick Setup
- Connection Type
- PPP over ATM/ PPP over Ethernet
- IP over ATM
- Bridging
- Status
- Overview
- ADSL Line
- ADSL BER Test
- Internet Connection
- Traffic Statistics
- DHCP Table
- Wireless Clients
- Routing Table
- ARP Table
- Advanced Setup
- Local Network – IP Address
- Local Network – DHCP Server
- Local Network – UPnP
- Local Network – IGMP Snooping
- Internet – Connections
- Adding a New One
- Internet – DNS Server
- Internet – IGMP Proxy
- Internet – ADSL
- IP Routing – Static Route
- Adding a New One
- Remove Static Route
- Example – Static Route
- IP Routing – Dynamic Routing
- Operation: There are two modes for you to choose, Active and Passive. Select Active for transmitting and receiving data, or select Passive for receiving data only.
- Virtual Server – Port Forwarding
- IP Address seen by Internet Users
- Add New Port Forwarding
- Virtual Server – Port Triggering
- Virtual Server – DMZ Host
- Virtual Server – Dynamic DNS
- Virtual Server – Static DNS
- NAT ALG Configuration
- Firewall
- Firewall – Bridge Filtering
- Firewall – IP Filtering
- Quality of Service
- Quality of Service – Bridge QoS
- Quality of Service – IP QoS
- Port Mapping
- Wireless
- Basic Settings
- Security
- For 64-bit WEP/128-bit WEP
- For 802.1X Wireless Network
- 802.1x environment Configuration
- For WPA (Wi-Fi Protected Access)
- For WPA-PSK; WPA2-PSK; Mixed WPA2/WPA-PSK
- For WPA-2; Mixed WPA2/WPA
- Access Control
- Repeater
- Management
- Diagnostics
- Management Accounts
- Management Control – From Remote
- Management Control – From Local
- TR-069 Client Configuration
- Identify the Validation of Certificate from ACS
- Internet Time
- System Log
- Configuring System Log
- Example
- System Log Configuration
- Viewing System Log – Remote Side (Server)
- Viewing System Log – Local Side (ADSL Router)
- Backup Config
- Update Firmware
- Reset Router
- UPnP for XP
- Chapter 5: Troubleshooting
- Problems with LAN
- Problems with WAN
- Problems with Upgrading
- Chapter 6: Glossary
- ARP (Address Resolution Protocol )
- DHCP (Dynamic Host Configuration Protocol)
- LAN (Local Area Network) & WAN (Wide Area Network)
- NAT (Network Address Translation) IP Address
- Private IP Address
- Public IP Address
- PVC (Permanent Virtual Circuit)
- RIP (Routing Information Protocol)
- UDP (User Datagram Protocol)
- Virtual Server
- VPI (Virtual Path Identifier) & VCI (Virtual Channel Identifier)
- Appendix A: Specifications
- Appendix B: Client Setup for 802.1x, WPA, and WPA-PSK
- Retreiving Client Certificate
- Enabling 802.1x Authentication and Security
- Enabling WPA Authentication and Security
- Enabling WPA-PSK Authentication and Security
Chapter 4: Web Configuration
97
Firewall
The firewall is a kind of software that interrupts the data between the Internet and
your computer. It is the TCP/IP equivalent of a security gate at the entrance to your
company. All data must pass through it, and the firewall (functions as a security
guard) will allow only authorized data to be passed into the LAN.
What the firewall can do? It can:
deny or permit any packet from passing through explicitly
distinguish between various interfaces and match on the following fields:
source and destination IP address
port
To keep track of the performance of IP Filter, a logging device is used. The device
supports logging of the TCP/UDP and IP packet headers and the first 129 bytes of
the packet (including headers) whenever a packet is successfully passed through or
blocked, and whenever a packet matches a rule being setup for suspicious packets.
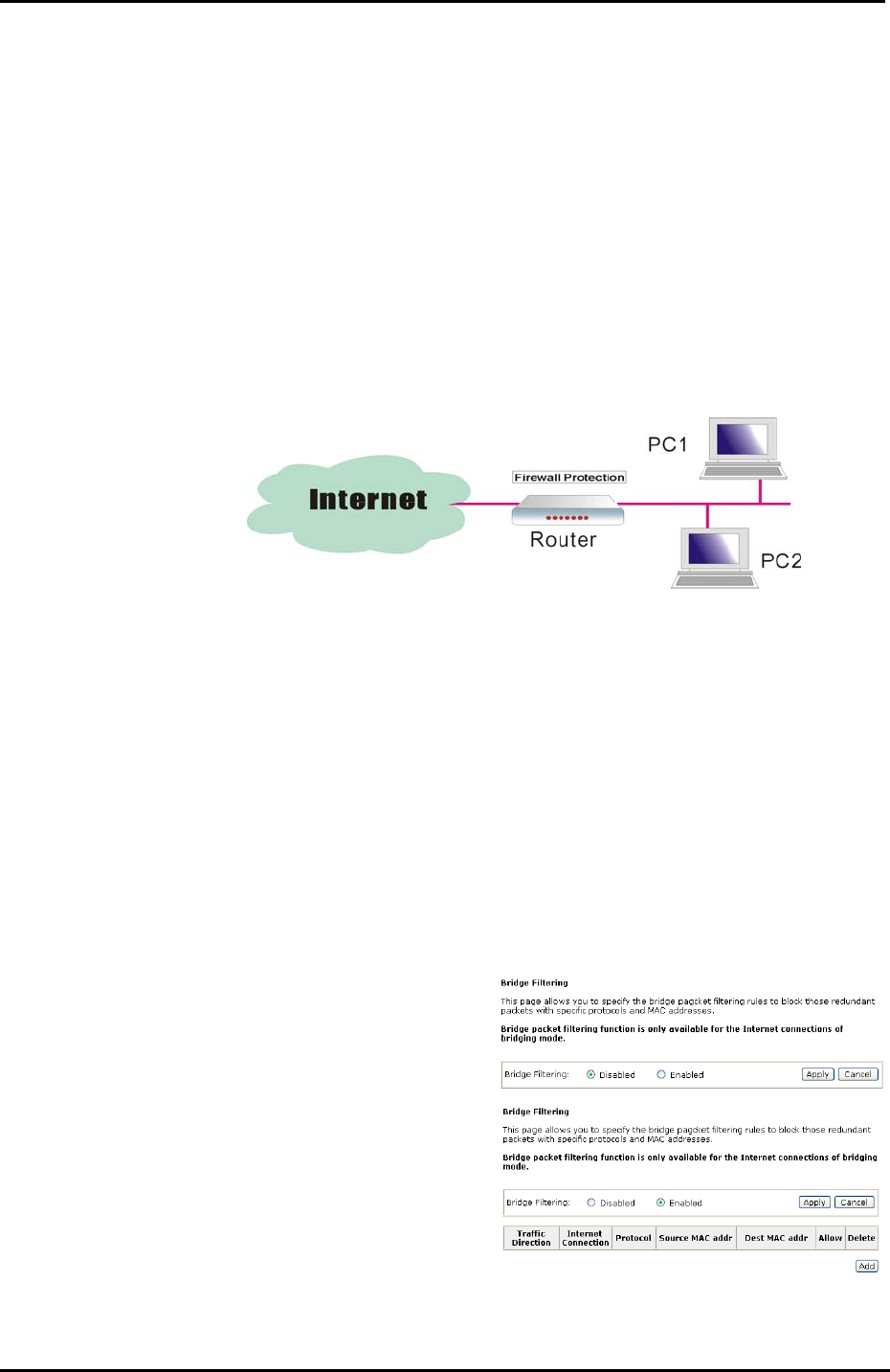
An example for firewall setup:
This picture shows the most common and easiest way to employ the firewall.
Basically, you can install a packet-filtering router at the Internet gateway and then
configures the filter rule in the router to block or filter protocols and addresses. The
systems behind the router usually have a direct access to the Internet; however
some dangerous services such as NIS and NFS are usually blocked.
For the security of your router, set the firewall is an important issue.
Firewall – Bridge Filtering
The bridge filtering mechanism provides a way for the users to define rules to
allow/deny packets through the bridge based on source MAC address and/or
destination MAC address. When bridge filtering is enabled, each packet is examined
against the each defined filter rules sequentially, and when a matched is determined,
the packets will be blocked.
This page allows you to define the bridge packet filtering rules to block those
redundant packets with specific protocols and MAC addresses.
Choose Disabled to disable the
bridge filtering function. Click Enabled
to monitor and block redundant
packets.
To initiate the Bridge Filtering rules,
select the Enabled radio button and
click Apply.
Click Add to configure a new bridge
filtering rule.
Note that the Add option is available
only when there is a bridge mode PVC
on this device.










