User guide
39
your computer. Many infiltrations try to obtain and send private data, or download other malicious applications to host
workstations. The Personal firewall allows you to detect and terminate such connections.
Display information about application allows you to define how applications will be displayed in the list of rules. The
following options are available:
Full path – Full path to the application’s executable.
Description – Description of the application.
Name – Name of the application's executable.
Select what type of rules will be displayed in the Rules to display list:
Only user defined rules – Displays only those rules created by the user.
User and pre-defined rules – Displays all user-defined and default pre-defined rules.
All rules (including system) – All rules are displayed.
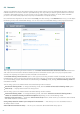
4.2.3.1 Rules setup
Rules setup allows you to view all rules applied to traffic generated by individual applications within trusted zones and
the Internet. By default, rules are added automatically according to user reactions to a new communication. To view
more information about an application at the bottom of this window, click the name of the application.
At the beginning of each line corresponding to a rule, there is a button allowing you to expand/collapse (+/-) the
information. Click on the name of the application in the Application / Rule column to display information about the
rule at the bottom of this window. You can use the contextual menu to change the display mode. The contextual menu
can be also used for adding, editing and deleting rules.
Trusted zone in/out – Actions related to incoming or outgoing communication within the Trusted zone.
Internet in/out – Internet connection related actions to incoming or outgoing communication.
For each type (direction) of communication, you can select the following actions:
Allow – To allow communication.
Ask – You will be prompted to allow or deny each time communication is established.
Deny – To deny communication.
Specific – Cannot be classified with respect to the other actions. For example, if an IP address or port is allowed
through the Personal firewall, it cannot be classified with certainty, whether incoming or outgoing communications
of a related application are allowed.
When installing a new application which accesses the network or when modifying an existing connection (remote side,
port number, etc.), a new rule must be created. To edit an existing rule, click the Rules tab and then Edit.