User guide
74
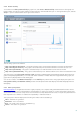
The following actions are available:
Compare – Compares two existing logs.
Create... – Creates a new log. Please wait until the ESET SysInspector log is complete (Status shown as Created).
Delete – Removes selected logs from the list.
After right-clicking one or more selected logs, the following options are available from the context menu:
Show – Opens the selected log in ESET SysInspector (same function as double-clicking a log).
Delete all – Deletes all logs.
Export... – Exports the log to an .xml file or zipped .xml.
4.6.6 ESET Live Grid
ESET Live Grid (the next generation of ESET ThreatSense.Net) is an advanced warning system against emerging threats
based on reputation. Utilizing real-time streaming of threat-related information from the cloud, ESET virus lab keeps
defenses up to date for a constant level of protection. User can check the reputation of running processes and files
directly from the program's interface or contextual menu with additional information available from ESET Live Grid.
There are two options:
1. You can decide to not enable the ESET Live Grid. You will not lose any functionality in the software, and you will still
receive the best protection that we offer.
2. You can configure the ESET Live Grid to submit anonymous information about new threats and where the new
threatening code is contained. This file can be sent to ESET for detailed analysis. Studying these threats will help ESET
update its threat detection capabilities.
ESET Live Grid will collect information about your computer related to newly-detected threats. This information may
include a sample or copy of the file in which the threat appeared, the path to that file, the filename, the date and time,
the process by which the threat appeared on your computer and information about your computer‘s operating system.
By default, ESET Smart Security is configured to submit suspicious files for detailed analysis to ESET‘s Virus Lab. Files
with certain extensions such as .doc or .xls are always excluded. You can also add other extensions if there are particular
files that you or your organization wants to avoid sending.
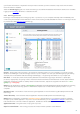
The ESET Live Grid's setup menu provides several options for enabling / disabling the ESET Live Grid that serves to
submit suspicious files and anonymous statistical information to ESET's labs. It is accessible from the Advanced setup
tree by clicking Tools > ESET Live Grid.
Participate in ESET Live Grid (recommended) – Enables / disables the ESET Live Grid that serves to submit suspicious
files and anonymous statistical information to ESET's labs.
Do not submit statistics – Select this option if you do not wish to submit anonymous information from the ESET Live
Grid about your computer. This information is related to newly detected threats, which may include the name of the
infiltration, information about the date and time it was detected, the version of ESET Smart Security, information about
your computer's operating system version and Location settings. The statistics are normally delivered to ESET's server
once or twice a day.
Do not submit files – Suspicious files, resembling infiltrations in their content or behavior, are not submitted to ESET
for analysis by means of ESET Live Grid technology.
Advanced setup... – Opens a window with additional ESET Live Grid settings.
If you have used ESET Live Grid before and have disabled it, there may still be data packages to send. Even after
deactivating, such packages will be sent to ESET on the next occasion. Afterwards, no further packages will be created.
4.6.6.1 Suspicious files
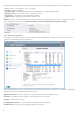
The Files tab in ESET Live Grid advanced setup allows you to configure how threats are submitted to ESET‘s Virus Lab
for analysis.
If you find a suspicious file, you can submit it for analysis to our ThreatLabs. If it is a malicious application, its detection
will be added to the next virus signature update.
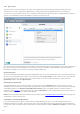
Exclusion filter – The Exclusion filter allows you to exclude certain files/folders from submission. The files listed will
never be sent to ESET's labs for analysis, even if they contain a suspicious code. For example, it may be useful to exclude
files which may carry confidential information, such as documents or spreadsheets. The most common file types are
excluded by default (.doc, etc.). You can add to the list of excluded files if desired.
Contact email (optional) – Your contact email can be included with any suspicious files and may be used to contact