User guide
20
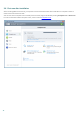
Computer scan setup... – Click to adjust the parameters of the on-demand scanner (manually executed scan).
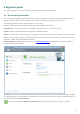
4.1.1 Antivirus and antispyware
Antivirus and antispyware protection guards against malicious system attacks by controlling file, email and Internet
communication. If a threat with malicious code is detected, the Antivirus module can eliminate it by first blocking it
and then cleaning, deleting or moving it to quarantine.
Scanner options for all protection modules (e.g. Real-time file system protection, Web access protection, ...) allow
you to enable or disable detection of the following:
Potentially unwanted applications (PUAs) are not necessarily intended to be malicious, but may affect the
performance of your computer in a negative way.
Read more about these types of applications in the glossary.
Potentially unsafe applications refers to legitimate commercial software that has the potential to be misused for
malicious purposes. Examples of potentially unsafe applications include remote access tools, password-cracking
applications, and keyloggers (programs recording each keystroke typed by a user). This option is disabled by
default.
Read more about these types of applications in the glossary.
Suspicious applications include programs compressed with packers or protectors. These types of protectors are
often exploited by malware authors to evade detection.
Anti-Stealth technology is a sophisticated system that provides the detection of dangerous programs such as
rootkits, which are able to hide themselves from the operating system. This means it is not possible to detect them
using ordinary testing techniques.
4.1.1.1 Real-time file system protection
Real-time file system protection controls all antivirus-related events in the system. All files are scanned for
malicious code at the moment they are opened, created or run on your computer. Real-time file system protection
is launched at system startup.
Real-time file system protection checks all types of media and is triggered by various system events such as
accessing a file. Using ThreatSense technology detection methods (as described in the ThreatSense engine
parameter setup section), Real-time file system protection can be configured to treat newly created files differently
than existing files. For example, you can configure Real-time file system protection to more closely monitor newly
created files.
To ensure a minimal system footprint when using real-time protection, files that have already been scanned are not
scanned repeatedly (unless they have been modified). Files are scanned again immediately after each virus
signature database update. This behavior is configured using Smart optimization. If this feature is disabled, all files
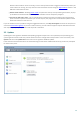
are scanned each time they are accessed. To modify this option, press F5 to open the Advanced setup window and
expand Computer > Antivirus and antispyware > Real-time file system protection. Click Setup... next to ThreatSense
engine parameter setup > Other and select or deselect Enable Smart optimization.
By default, Real-time file system protection launches at system startup and provides uninterrupted scanning. In
special cases (for example, if there is a conflict with another real-time scanner), real-time protection can be
disabled by deselecting Start Real-time file system protection automatically in the Real-time file system protection
section of Advanced setup.