User guide
63
4.3.3.4.1.2 Excluded certificates
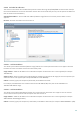
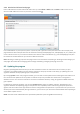
The Excluded certificates section contains certificates that are considered safe. The content of encrypted
communications utilizing the certificates in the list will not be checked for threats. We recommend only excluding
web certificates that are guaranteed to be safe and where communication utilizing the certificates does not need to
be checked. To delete selected items from the list, click Remove. Click Show (or double-click the certificate) to
display information about the selected certificate.
4.3.3.4.1.3 Encrypted SSL communication
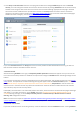
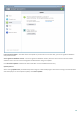
If the computer is configured for SSL protocol scanning, a dialog window prompting you to choose an action may be
opened when there is an attempt to establish an encrypted communication (using an unknown certificate). The
dialog window contains the following information: name of the application that initiated the communication and
name of the certificate used.
If the certificate is not located in the Trusted Root Certification Authorities store, it is considered to be untrusted.
The following actions are available for certificates:
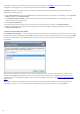
Yes – The certificate will be temporarily marked as trusted – the alert window will not be displayed on the next
attempt to use the certificate for the duration of the current session.
Yes, always – Marks the certificate as trusted and adds it to the list of trusted certificates – no alert windows will be
displayed for trusted certificates.
No – Marks the certificate as untrusted for the current session – the alert window will be displayed on the next
attempt to use the certificate.
Exclude – Adds the certificate to the list of excluded certificates – data transferred over the given encrypted channel
will not be checked at all.
4.3.4 Anti-Phishing protection
The term phishing defines a criminal activity that uses social engineering (the manipulation of users in order to
obtain confidential information). Phishing is often used to gain access to sensitive data such as bank account
numbers, PIN numbers and more. Read more about this activity in the glossary. ESET Smart Security provides anti-
phishing protection, web pages known to distribute this type of content can be blocked.
We strongly recommend that you enable Anti-Phishing in ESET Smart Security. This option can be accessed from
Advanced setup (F5) by navigating to Web and email > Anti-Phishing protection.
Please see also our Knowledgebase article for an updated and more detailed version of this help page.
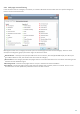
Accessing a phishing website
When you access a phishing website, you will receive the following dialog in your web browser. By clicking Proceed
to the site (not recommended), you will be able to access the website without a warning message.