User guide
77
4.6.1 Log files
Log files contain information about all important program events that have occurred and provide an overview of
detected threats. Logging is an essential part of system analysis, threat detection and troubleshooting. Logging is
performed actively in the background with no user interaction. Information is recorded based on the current log
verbosity settings. It is possible to view text messages and logs directly from the ESET Smart Security environment,
as well as to archive logs.
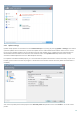
Log files are accessible from the main program window by clicking Tools > Log files. Select the desired log type from
the Log drop-down menu. The following logs are available:
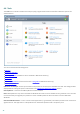
Detected threats – The threat log offers detailed information about infiltrations detected by ESET Smart Security .
The information includes the time of detection, name of infiltration, location, the performed action and the name
of the user logged in at the time the infiltration was detected. Double-click any log entry to display its details in a
separate window.
Events – All important actions performed by ESET Smart Security are recorded in the event log. The event log
contains information about events and errors that have occurred in the program. It is designed for system
administrators and users to solve problems. Often the information found here can help you find a solution for a
problem occurring in the program.
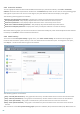
Computer scan – Results of all completed manual or planned scans are displayed in this window. Each line
corresponds to a single computer control. Double-click any entry to view details of the respective scan.
HIPS – Contains records of specific HIPS rules which were marked for recording. The protocol shows the
application that triggered the operation, the result (whether the rule was permitted or prohibited) and the
created rule name.
Personal firewall – The firewall log displays all remote attacks detected by the Personal firewall. Here you will
find information about any attacks on your computer. The Event column lists the detected attacks. The Source
column tells you more about the attacker. The Protocol column reveals the communication protocol used for the
attack. Analysis of the firewall log may help you to detect system infiltration attempts in time to prevent
unauthorized access to your system.
Filtered websites – This list is useful if you want to view a list of websites that were blocked by Web access
protection or Parental control. In these logs you can see time, URL address, user and application that created a
connection to the particular website.
Antispam protection – Contains records related to email messages that were marked as spam.
Parental control – Shows web pages blocked or allowed by Parental control. The Match type and Match values
columns tell you how the filtering rules were applied.
Device control – Contains records of removable media or devices that were connected to the computer. Only
devices with respective Device control rules will be recorded to the log file. If the rule does not match a
connected device, a log entry for a connected device will not be created. Here you can also see details such as
device type, serial number, vendor name and media size (if available).
In each section, the displayed information can be directly copied to the clipboard (keyboard shortcut Ctrl + C) by
selecting the entry and clicking Copy. To select multiple entries, the CTRL and SHIFT keys can be used.