User guide
82
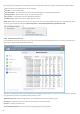
The ESET Live Grid setup menu provides several options for enabling / disabling ESET Live Grid, which serves to
submit suspicious files and anonymous statistical information to ESET labs. It is accessible from the Advanced setup
tree by clicking Tools > ESET Live Grid.
Participate in ESET Live Grid (recommended) – Enables / disables ESET Live Grid, which serves to submit suspicious
files and anonymous statistical information to ESET labs.
Do not submit statistics – Select this option if you do not want to submit anonymous information gathered by ESET
Live Grid about your computer. This information is related to newly detected threats, which may include the name
of the infiltration, information about the date and time it was detected, the version of ESET Smart Security,
information about your computer's operating system version and Location settings. The statistics are normally
delivered to ESET servers once or twice a day.
Do not submit files – Suspicious files, resembling infiltrations in their content or behavior, are not submitted to ESET
for analysis by means of ESET Live Grid technology.
Advanced setup... – Opens a window with additional ESET Live Grid settings.
If you have used ESET Live Grid before and have disabled it, there may still be data packages to send. Even after
deactivating, such packages will be sent to ESET on the next occasion. Afterwards, no further packages will be
created.
4.6.6.1 Suspicious files
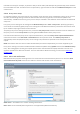
The Files tab in ESET Live Grid advanced setup allows you to configure how threats are submitted to ESET Virus Labs
for analysis.
If you find a suspicious file, you can submit it for analysis to our ThreatLabs. If it is a malicious application, its
detection will be added to the next virus signature update.
Exclusion filter – The Exclusion filter allows you to exclude certain files/folders from submission. The files listed will
never be sent to ESET's labs for analysis, even if they contain a suspicious code. For example, it may be useful to
exclude files that may carry confidential information, such as documents or spreadsheets. The most common file
types are excluded by default (.doc, etc.). You can add to the list of excluded files if desired.
Contact email (optional) – Your contact email can be included with any suspicious files and may be used to contact
you if further information is required for analysis. Please note that you will not receive a response from ESET unless
more information is needed.
Select Enable logging to create an event log to record file and statistical information submissions. This will enable
logging to the Event log when files or statistics are sent.