Network Router User Manual
Table Of Contents
- Contents
- Introduction
- Configuring a FortiGate SSL VPN
- Comparison of SSL and IPSec VPN technology
- SSL VPN modes of operation
- Topology
- Configuration overview
- Configuring the SSL VPN client
- Configuring SSL VPN settings
- Enabling SSL VPN connections and editing SSL VPN settings
- Specifying a port number for web portal connections
- Specifying an IP address range for tunnel-mode clients
- Enabling strong authentication through security certificates
- Specifying the cipher suite for SSL negotiations
- Setting the idle timeout setting
- Setting the client authentication timeout setting
- Adding a custom caption to the web portal home page
- Adding WINS and DNS services for clients
- Redirecting a user group to a popup window
- Customizing the web portal login page
- Configuring user accounts and SSL VPN user groups
- Configuring firewall policies
- Configuring SSL VPN event-logging
- Monitoring active SSL VPN sessions
- Configuring SSL VPN bookmarks and bookmark groups
- SSL VPN host OS patch check
- Granting unique access permissions for SSL VPN tunnel user groups
- SSL VPN virtual interface (ssl.root)
- SSL VPN dropping connections
- Working with the web portal
- Index
FortiOS v3.0 MR7 SSL VPN User Guide
44 01-30007-0348-20080718
Configuring firewall policies Configuring a FortiGate SSL VPN
• specifying the level of SSL encryption to use and the authentication method
• binding the user group to the firewall policy
The following topics are included in this section:
• Configuring firewall addresses
• Configuring tunnel-mode firewall policies
• Configuring SSL VPN event-logging
• Monitoring active SSL VPN sessions
Configuring firewall addresses
Configuring the firewall addresses for web-only and tunnel mode connections
involves specifying the IP source/host and destination addresses:
Web-only mode:
• For the source address, select the predefined address “all” in the firewall
encryption policy to refer to web-only mode clients.
• The destination address corresponds to the IP address or addresses that
remote clients need to access. The destination address may correspond to
an entire private network (behind the FortiGate unit), a range of private IP
addresses, or the private IP address of a server or host.
Tunnel mode:
• The source address corresponds to the public IP address that can be
connected to the FortiGate unit. This address is used to restrict who can
access the FortiGate unit.
• The destination address corresponds to the IP address or addresses that
remote clients need to access. The destination address may correspond to
an entire private network (behind the FortiGate unit), a range of private IP
addresses, or the private IP address of a server or host.
Configuring Web-only firewall policies
To specify the destination IP address
1 Go to Firewall > Address and select Create New.
2 In the Address Name field, type a name that represents the local network,
server(s), or host(s) to which IP packets may be delivered (for example,
Subnet_1).
3 From the Type list, select Subnet/IP Range.
4 In the Subnet/IP Range field, type the corresponding IP address and subnet mask
(for example, 172.16.10.0/24).
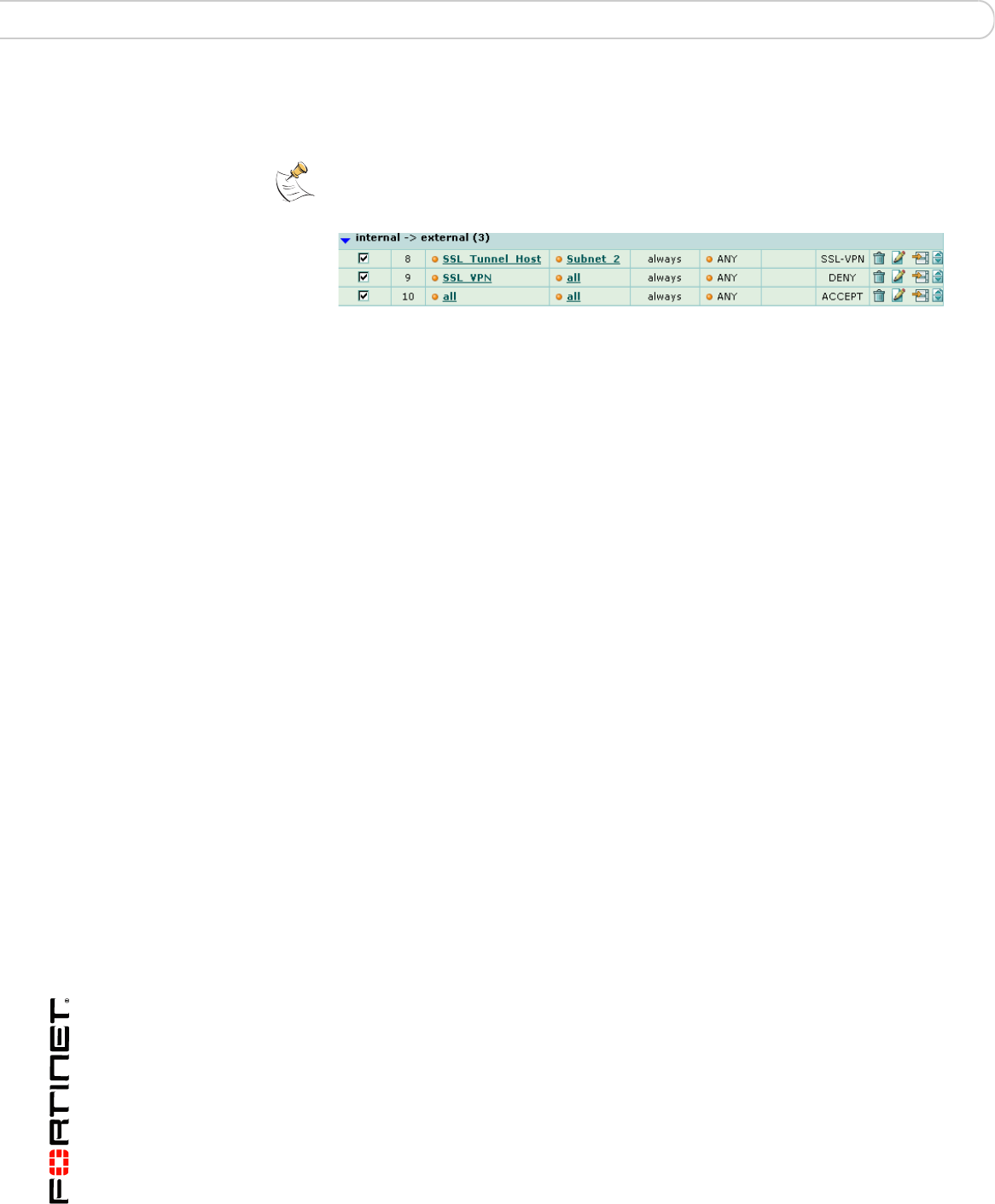
Note: In tunnel mode, it is necessary to create a DENY firewall policy that immediately
follows the SSL VPN policy. If this policy is not created, SSL VPN tunnels will use other
ACCEPT firewall policies. See the order of the Firewall policies below: