User Manual
Table Of Contents
- Introduction
- Chapter 2 Getting Started
- Chapter 3 Camera Management
- Chapter 4 Camera Settings
- Chapter 5 Live View
- Chapter 6 PTZ Control
- Chapter 7 Storage
- 7.1 Storage Device Management
- 7.2 Storage Mode
- 7.3 Recording Parameters
- 7.4 Configure Recording Schedule
- 7.5 Configure Continuous Recording
- 7.6 Configure Motion Detection Triggered Recording
- 7.7 Configure Event Triggered Recording
- 7.8 Configure Alarm Triggered Recording
- 7.9 Configure POS Event Triggered Recording
- 7.10 Configure Picture Capture
- 7.11 Configure Holiday Recording and Capture
- 7.12 Configure Redundant Recording and Capture
- Chapter 8 Disk Array (RAID)
- Chapter 9 File Management
- Chapter 10 Playback
- Chapter 11 Event and Alarm Settings
- 11.1 Configure Arming Schedule
- 11.2 Configure Alarm Linkage Actions
- 11.3 Configure Motion Detection Alarms
- 11.4 Configure Video Loss Alarms
- 11.5 Configure Video Tampering Alarms
- 11.6 Configure Sensor Alarms
- 11.7 Configure Exceptions Alarms
- 11.8 Setting Alarm Linkage Actions
- 11.9 Trigger or Clear Alarm Output Manually
- Chapter 12 VCA Event Alarm
- 12.1 Face Detection
- 12.2 Vehicle Detection
- 12.3 Line Crossing Detection
- 12.4 Intrusion Detection
- 12.5 Region Entrance Detection
- 12.6 Region Exiting Detection
- 12.7 Unattended Baggage Detection
- 12.8 Object Removal Detection
- 12.9 Audio Exception Detection
- 12.10 Sudden Scene Change Detection
- 12.11 Defocus Detection
- 12.12 PIR Alarm
- 12.13 Thermal Camera Detection
- Chapter 13 Smart Analysis
- Chapter 14 POS Configuration
- Chapter 15 Network Settings
- Chapter 16 Hot Spare Device Backup
- Chapter 17 User Management and Security
- Chapter 18 System Service Maintenance
- Chapter 19 General System Settings
- Chapter 20 Appendix
Network Video Recorder User Manual
132
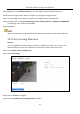
Figure 12-4 Intrusion Detection
Step 3 Select a camera to configure.
Step 4 Check Enable Intrusion Detection.
Step 5 Optionally, check Save VCA Picture to save the captured intrusion detection pictures.
Step 6 Follow these steps to set the detection rules and detection areas.
1) Select a Virtual Panel to configure. Up to 4 virtual panels are selectable.
2) Drag the sliders to set Time Threshold, Sensitivity, and Percentage.
Time Threshold: The time an object loiter in the region. When the duration of the object
in the defined detection area exceeds the threshold, the device will trigger an alarm. Its
range is [1s-10s].
Sensitivity: The size of the object that can trigger the alarm. The higher the value is, the
more easily the detection alarm will be triggered. Its range is [1-100].
Percentage: The ratio of the in-region part of the object that can trigger the alarm. For
example, if the percentage is 50%, when the object enters the region and occupies half of
the whole region, the device will trigger an alarm. Its range is [1-100].
3) Click Draw Region and draw a quadrilateral in the preview window by specifying four vertices of
the detection region.
Step 7 Set the arming schedule. Refer to Chapter 11.1 Configure Arming Schedule.
Step 8 Set the linkage actions. Refer to Chapter 11.2 Configure Alarm Linkage Actions.
Step 9 Click Apply.