Intel Unite Solution - Enterprise Deployment Guide
Intel Unite® Solution Enterprise Deployment Guide v3.1.7 78 of 83
Appendix C. Intel Unite Solution - Security
Overview
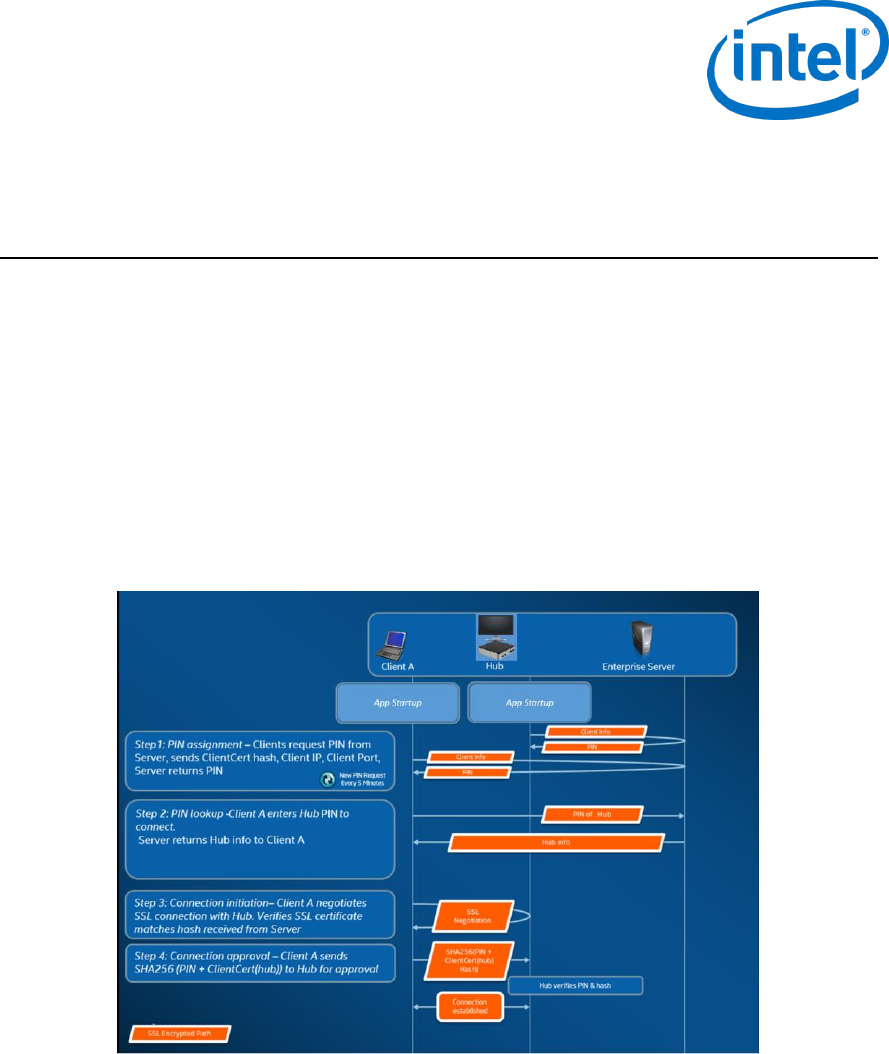
Intel Unite Software - Security Flow
This section briefly describes the security aspects of Intel Unite application. Security aspects of the
connection are discussed for the following four steps:
1. PIN assignment
2. PIN lookup
3. Connection initiation
4. Connection approval
The following image contains a high level overview of how the Client (with Intel vPro technology) and Hub
applications securely receive PINs from the Enterprise Server, resolve PINs, and establish a connection.