HP SmartStream 3D Command Center 3.2 installation and troubleshooting guide
Technical Newsletter | HP SmartStream 3D Command Center 3.2 installation and troubleshooting guide
22
Configure Command Center to support SSL Bump for traffic inspection
You need to add to the public certificate from the SSL inspector that generates the ad-hoc certificates for all sites and
swaps them from the original ones. Once you add this certificate to the Command Center Server, it will start to trust the
traffic from the SSL inspector.
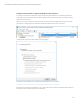
Open the local computer certificate console (certlm.msc) and check if the public certificate of the device performing the
SSL inspection is already added to the Trusted Root Certification Authorities folder. If not, please add it.
If already added, export the certificate as Base-64 and save the file.
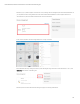
Move the exported certificate to user-certificates in the Application directory, see full path:
C:\Windows\ServiceProfiles\LocalService\AppData\Roaming\HP\3DSSCC\user-certificates
Restart the server. Once the Command Center server processes start again, it will load this certificate, and the traffic from
the SSL/TLS inspector will be trusted as if it was untampered.