Data Execution Prevention - White Paper, 2nd Edition
3
Data Execution Prevention (DEP)
What does Data Execution Prevention do?
Data Execution Prevention (DEP) is a set of hardware and software technologies that perform checks on
memory to help protect against malicious code and viruses. In Windows XP SP2, DEP is enforced by both
hardware and software.
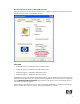
Data Execution Prevention Exception Message Box
If an application or driver attempts to execute code from an area where it should not on a DEP-protected
computer, Windows displays the following exception error:
Hardware-Enforced DEP
Hardware-enforced DEP marks all memory locations as non-executable (you cannot execute code in this
portion of memory) unless the location explicitly contains executable code. There is a class of attacks that
attempts to insert and execute code from non-executable memory locations. DEP helps prevent these
attacks by intercepting them and displaying the DEP message box.
Hardware-enforced DEP relies on processor hardware to mark memory with an attribute that indicates
that code should not be executed from that memory. The actual hardware implementation of DEP varies
by processor architecture. However, processors that support hardware-enforced DEP are capable of rais-
ing an exception when code is executed from a memory location where it should not be executed.
Both Advanced Micro Devices™ (AMD) and Intel® Corporation have defined and shipped Windows-
compatible architectures that support DEP. Beginning with Windows XP Service Pack 2, the 32-bit version
of Windows utilizes the no-execute page-protection (NX) processor feature as defined by AMD and the
Execute Disable (XD) bit feature as defined by Intel. AMD also refers to this feature as “Enhanced Virus
Protection.” To use these processor features, the processor must run in Physical Address Extension (PAE)
mode. HP ships Windows XP with PAE enabled.