MSM7xx Controllers Configuration Guide v6.4.0
DescriptionParameter
example, one use for this feature could be to block access to a popular
protocol, then prompt the user for additional fees to activate support.
• WARN: Reject traffic matching this rule and return an HTTP error message
(which is not customizable) indicating that access to the site is not
allowed by the network.
Specify the protocol to check: tcp, udp, icmp, allprotocol
Specify one of the following:address
• IP address or domain name (up to 107 characters in length)
• Subnet address. Include the network mask as follows: address/
subnet mask For example: 192.168.30.0/24
• Use the keyword all to match any address.
• Use the wildcard symbol * to match any sequence of characters at the
beginning or the end of a domain name. For example:
*.mydomain matches any host on the domain.mydomain.
myhost.* matches myhost at any domain. For example,
myhost.com or myhost.ca
• Use the keyword none if the protocol does not take an address range
(ICMP for example).
Specify a specific port to check or a port range as follows:port
• none - Used with ICMP (since it has no ports).
• all - Check all ports.
• 1-65535[:1-65535] - Specify a specific port or port range.
NOTE: If you choose all possible protocols for an access-list definition,
then you must supply all ports as well.
Specify the name of the user account the controller will send billing
information to for this rule. Account names must be unique and can be
up to 32 characters in length.
account
Specify time between interim accounting updates. If you do not enable
this option, accounting information is only sent when a user connection
is terminated. Range: 5 to 99999 seconds in 15 second increments.
interval
Access list example
This example illustrates how access lists can be used to control access to network resources for
different groups of users at a fictitious university campus.
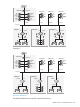
Topology
The following two topologies show potential wireless deployments for the campus using different
types of HP equipment. In both cases, a RADIUS server is used to store configuration attributes for
the public access network. Although the topologies are slightly different, the same access list
definitions are used for both installations.
Topology 1:
464 Working with RADIUS attributes