MSM7xx Controllers Configuration Guide v6.4.0
20 Public/guest network access
Introduction
The Public/Guest Network Access feature enables you to provide controlled network access for a
variety of deployments. Some common applications of this feature are:
• Providing Internet access to wireless customers in airports, restaurants, train stations, conference
halls, etc.
• Providing wireless and wired access to staff and guests in hospitals, corporations, and
government buildings.
• Providing wireless and wired access to students, staff, and teachers in schools and universities.
• Providing outdoor wireless access for an entire town, enabling city workers, police, fire, public
security, and the general public to connect.
This chapter provides describes the public/guest network access feature and how it can be used.
For detailed information on the RADIUS attributes that can be used to customize the public access
interface, see “Working with RADIUS attributes” (page 435)
Key concepts
Access control
When the Access control option is enabled on a VSC, it creates an access-controlled VSC. This
means that for all traffic on the VSC, the controller acts as the gatekeeper between two distinct
network segments: the public network and the protected network.
• Public network: Access to the public network and its resources is generally made available
to all unauthenticated wireless users once they successfully connect to the wireless network.
Access is also generally made available to unauthenticated wired users on any network that
is connected to the controller LAN port.
• Protected network: Access to the protected network is restricted by the controller and typically
requires that users be authenticated by the controller before they gain access. Various
authentication methods are available (HTML-based, MAC-based, 802.1X). The most commonly
used method is HTML-based, which enables users to login through their Web browsers via
the public access interface Login page. The controller can validate user login credentials using
locally defined user accounts or by using the services of a third-party authentication server
(RADIUS or Active Directory).
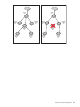
The following diagrams illustrates a basic setup in which a wireless user is authenticated by an
access-controlled VSC and then gains access to a corporate network.
Protected network
Public network
AP
User lo
gs
in
A
c
ce
s
s to
n
e
tw
o
rk is
g
ra
n
te
d
Access
controlled
VSC
Corporate
network
Controller
Router
396 Public/guest network access