MSM7xx Controllers Configuration Guide v6.4.0
For more information on access control, see “Configuring global access control options” (page
399).
NOTE: If authentication is not enabled on a VSC, all users connected to the VSC can access the
protected network.
Access lists
An access list is a set of rules that governs how the controller manages access to the public and
private network resources. You can create multiple access lists, each with multiple rules, enabling
you to create public areas on your network that all users can browse, and protected areas that
are restricted to specific user accounts or groups.
For more information, see “Access list” (page 484).
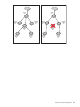
In the following example, access lists are defined to allow the following levels of access:
• Unauthenticated users can access Network 1.
• Authenticated employees can access Network 2 and the Internet.
• Authenticated guests can access the Network 3 and the Internet.
Protected networks
Public networks
AP
Access
controlled
VSC
Network 2
Controller
Network 1
Network 3
Internet
Unauthenticated user
Authenticated employee
The public access interface
The public access interface is the sequence of Web pages through which access-controlled users
can log in, log out, and view the status of their wireless connections to the public access network.
By default, these Web pages are hosted on the controllers Web server. However, pages can also
be hosted on external servers for added flexibility. The pages, error messages, images, and
workflow are all customizable.
Standard pages are provided for common tasks such as login, service purchase, and display of
session information. As well, advertisements can be displayed if required.
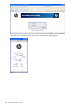
When a wireless user attempts to browse a Web site that is on the protected network, the user is
redirected to the public access interface Login page. The default page looks similar to this:
Key concepts 397