F3215-HP Load Balancing Module System Maintenance Configuration Guide-6PW101
49
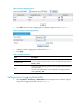
Figure 19 Attack prevention log configuration page
Table 16 Configuration items
Item Descri
p
tion
Time Time when the attack was detected.
Type
Attack type.
Interface
Interface that receives the attack packets.
Source IP
Source IP address of the attack packets.
Source MAC
Source MAC address of the attack packets.
Destination IP
Destination IP address of the attack packets.
Destination MAC
Destination MAC address of the attack packets.
Speed
Connection speed of the attack.
Displaying blacklist logs
Select Log Report > Report > Blacklist Log from the navigation tree to enter the page as shown in Figure
20. Table 17 desc
ribes the configuration items.
Figure 20 Blacklist log configuration page