F3726, F3211, F3174, R5135, R3816-HP Firewalls and UTM Devices Access Control Configuration Guide-6PW100
34
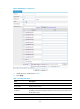
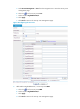
Item Descri
p
tion
Interface
Interface
Set the interfaces to be added to the security zone.
The interfaces that have been added to a security zone are in the selected status,
and the interfaces that can be added but have not been added to a security zone
are in the non-selected status.
VLAN
If the interfaces added to the security zone are Layer 2 Ethernet interfaces, you
must specify the range of the VLANs to be added to the security zone. The VLANs
must belong to the VD to which the security zone belongs and have not been
added to other security zones.
131BSecurity zone configuration example
274BNetwork requirements
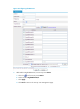
A company deploys a firewall (see 574HFigure 27) to connect its internal network to the Internet, and it needs
to provide WWW service and FTP service for external users. The security policy is to allow internal users
to access the WWW and FTP servers and the Internet and to allow external users to access only the
servers.
Prepare the firewall for zone-based security policy deployment.
Figure 27 Network diagram
275BConfiguration considerations
Three security zones are needed: one for the internal users, one for the servers, and one for the external
users, in the order of priority (from high to low). The default zones Trust, DMZ, and Untrust can answer
the requirements for security zones.
To prepare the firewall for zone-based security policy deployment, configure the firewall as follows:
• Add the port connected to the internal network (GigabitEthernet 0/3) to security zone Trust.
• Add the port connected to the Internet (GigabitEthernet 0/2) to security zone Untrust.
• Deploy the servers in security zone DMZ, and add the port connected to the servers
(GigabitEthernet 0/1) to security zone DMZ.
276BConfiguration procedure
1. Add interface GigabitEthernet 0/3 to security zone Trust: