F3726, F3211, F3174, R5135, R3816-HP Firewalls and UTM Devices Access Control Configuration Guide-6PW100
41
To achieve the goal, configure the firewall as follows:
• Add the interface connected to the internal network (GigabitEthernet 0/0) to security zone Trust.
• Add the interface connected to the Internet (GigabitEthernet 0/2) to security zone Untrust.
• Deploy the servers in security zone DMZ, and add the interface connected to the servers
(GigabitEthernet 0/1) to security zone DMZ.
• Create interzone instances and enable ASPF for the instances.
279BConfiguration procedure
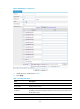
# Add interface GigabitEthernet 0/0 to security zone Trust.
<Firewall> system-view
[Firewall] zone name Trust
[Firewall-zone-Trust] import interface gigabitethernet 0/0
[Firewall-zone-Trust] quit
# Add interface GigabitEthernet 0/1 to security zone DMZ.
[Firewall] zone name DMZ
[Firewall-zone-DMZ] import interface gigabitethernet 0/1
[Firewall-zone-DMZ] quit
# Add interface GigabitEthernet 0/2 to security zone Untrust.
[Firewall] zone name Untrust
[Firewall-zone-Untrust] import interface gigabitethernet 0/2
[Firewall-zone-Untrust] quit
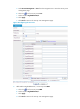
# Create an interzone instance with source security zone Trust and destination security zone Untrust, and
enable ASPF for the instance.
[Firewall] interzone source Trust destination Untrust
[Firewall-interzone-Trust-Untrust] firewall aspf enable
[Firewall-interzone-Trust-Untrust] quit
# Create an interzone instance with source security zone Trust and destination security zone DMZ, and
enable ASPF for the instance.
[Firewall] interzone source Trust destination DMZ
[Firewall-interzone-Trust-DMZ] firewall aspf enable
[Firewall-interzone-Trust-DMZ] quit
280BVerifying the configuration
After the configuration, internal hosts should be able to access Internet resources and the resources in
security zone DMZ, and access requests initiated from the Internet should be denied.