F3726, F3211, F3174, R5135, R3816-HP Firewalls and UTM Devices Attack Protection Configuration Guide-6PW100
32
The firewall discards all packets from Host D before you remove the blacklist entry for the host. If the
firewall receives packets from Host C, the firewall discards all packets from Host C within 50 minutes.
After 50 minutes, the firewall forwards packets from Host C normally.
The firewall outputs an alarm log and adds the IP address to the blacklist when detecting a scanning
attack from the untrusted zone. You can select Intrusion Detection > Blacklist from the navigation tree to
view the blacklist entry automatically added by scanning attack protection.
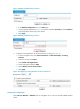
62BDisplaying intrusion detection statistics
1. From the navigation tree, select Intrusion Detection > Statistics to enter the intrusion detection
statistics page, as shown in
307HFigure 40.
2. Select a zone to view the counts of attacks and the counts of dropped packets in the security zone.
Descriptions of attack types are shown in
308HTable 12.
Figure 40 Intrusion detection statistics
Table 12 Attack types description
Attack t
yp
e Descri
p
tion
Fraggle
A Fraggle attack occurs when an attacker sends a large number of UDP echo requests
with the UDP port number of 7 or Chargen packets with the UDP port number of 19.
This results in a large quantity of junk replies, and finally exhausts the bandwidth of the
target network.
ICMP Redirect
An ICMP redirect attacker sends ICMP redirect messages to a target to modify its
routing table. This interferes with the normal forwarding of IP packets.