F3726, F3211, F3174, R5135, R3816-HP Firewalls and UTM Devices NAT and ALG Configuration Guide-6PW100
Table Of Contents
- Title Page
- Table of Contents
- Configuring NAT
- Overview
- Configuration guidelines
- Configuring NAT in the Web interface
- Recommended configuration procedure
- Creating an address pool
- Configuring dynamic NAT on an interface
- Creating a static address mapping
- Enabling static NAT on an interface
- Configuring an internal server
- Configuring ACL-based NAT on the internal server
- Configuring DNS mapping
- NAT configuration example
- Internal server configuration example
- Configuring NAT at the CLI
- NAT configuration task list
- Configuring static NAT
- Configuring dynamic NAT
- Configuring an internal server
- Configuring ACL-based NAT on an internal server
- Configuring DNS mapping
- Displaying and maintaining NAT
- One-to-one static NAT configuration example
- Dynamic NAT configuration example
- Common internal server configuration example
- NAT DNS mapping configuration example
- Troubleshooting NAT
- Configuring NAT-PT
- Feature and hardware compatibility
- Overview
- NAT-PT configuration task list
- Configuration prerequisites
- Enabling NAT-PT
- Configuring a NAT-PT prefix
- Configuring IPv4/IPv6 address mappings on the IPv6 side
- Configuring IPv4/IPv6 address mappings on the IPv4 side
- Setting the ToS field after NAT-PT translation
- Setting the traffic class field after NAT-PT translation
- Configuring static NAPT-PT mappings of IPv6 servers
- Displaying and maintaining NAT-PT
- NAT-PT configuration examples
- Troubleshooting NAT-PT
- NAT444
- Configuring ALG
- Support and other resources
- Index
44
<RouterA> system-view
[RouterA] interface gigabitethernet 0/1
[RouterA-GigabitEthernet0/1] ip address 8.0.0.2 255.255.255.0
[RouterA-GigabitEthernet0/1] quit
# Configure a static route to subnet 9.0.0.0/24.
[RouterA] ip route-static 9.0.0.0 24 8.0.0.1
3. Configure Router B on the IPv6 side:
# Enable IPv6.
<RouterB> system-view
[RouterB] ipv6
# Configure an IP address for GigabitEthernet 0/1.
[RouterB] interface gigabitethernet 0/1
[RouterB-GigabitEthernet0/1] ipv6 address 2001::2/64
[RouterB-GigabitEthernet0/1] quit
# Configure a static route to the subnet with the NAT-PT prefix.
[RouterB] ipv6 route-static 3001:: 16 2001::1
79BConfiguring static mappings on the IPv4 side and the IPv6 side
142BNetwork requirements
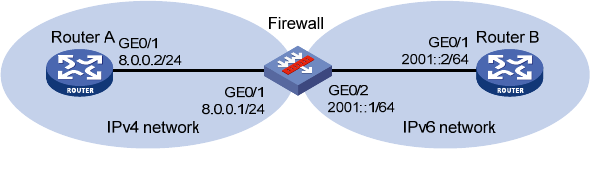
As shown in 273HFigure 33, Router B with IPv6 address 2001::2/64 on an IPv6 network can communicate
with Router A with IPv4 address 8.0.0.2/24 on an IPv4 network.
To meet the preceding requirement, you need to configure Firewall that is deployed between the IPv4
network and IPv6 network as a NAT-PT device, and configure static mappings on the IPv4 side and IPv6
side on Firewall, so that Router A and Router B can communicate with each other.
Figure 33 Network diagram
143BConfiguration procedure
1. Configure Firewall:
# Configure interface addresses and enable NAT-PT on the interfaces.
<Firewall> system-view
[Firewall] ipv6
[Firewall] interface gigabitethernet 0/1
[Firewall-GigabitEthernet0/1] ip address 8.0.0.1 255.255.255.0
[Firewall-GigabitEthernet0/1] natpt enable
[Firewall-GigabitEthernet0/1] quit
[Firewall] interface gigabitethernet 0/2
[Firewall-GigabitEthernet0/2] ipv6 address 2001::1/64
[Firewall-GigabitEthernet0/2] natpt enable
[Firewall-GigabitEthernet0/2] quit










