F3726, F3211, F3174, R5135, R3816-HP Firewalls and UTM Devices NAT and ALG Configuration Guide-6PW100
Table Of Contents
- Title Page
- Table of Contents
- Configuring NAT
- Overview
- Configuration guidelines
- Configuring NAT in the Web interface
- Recommended configuration procedure
- Creating an address pool
- Configuring dynamic NAT on an interface
- Creating a static address mapping
- Enabling static NAT on an interface
- Configuring an internal server
- Configuring ACL-based NAT on the internal server
- Configuring DNS mapping
- NAT configuration example
- Internal server configuration example
- Configuring NAT at the CLI
- NAT configuration task list
- Configuring static NAT
- Configuring dynamic NAT
- Configuring an internal server
- Configuring ACL-based NAT on an internal server
- Configuring DNS mapping
- Displaying and maintaining NAT
- One-to-one static NAT configuration example
- Dynamic NAT configuration example
- Common internal server configuration example
- NAT DNS mapping configuration example
- Troubleshooting NAT
- Configuring NAT-PT
- Feature and hardware compatibility
- Overview
- NAT-PT configuration task list
- Configuration prerequisites
- Enabling NAT-PT
- Configuring a NAT-PT prefix
- Configuring IPv4/IPv6 address mappings on the IPv6 side
- Configuring IPv4/IPv6 address mappings on the IPv4 side
- Setting the ToS field after NAT-PT translation
- Setting the traffic class field after NAT-PT translation
- Configuring static NAPT-PT mappings of IPv6 servers
- Displaying and maintaining NAT-PT
- NAT-PT configuration examples
- Troubleshooting NAT-PT
- NAT444
- Configuring ALG
- Support and other resources
- Index
1
1BConfiguring NAT
6B
Overview
Network Address Translation (NAT) provides a way to translate an IP address in the IP packet header to
another IP address. NAT enables a large number of private users to access the Internet by using a small
number of public IP addresses. NAT effectively alleviates the depletion of IP addresses.
A private IP address is used only in an internal network, whereas a public or external IP address is used
on the Internet and is globally unique.
According to RFC 1918, three blocks of IP addresses are reserved for private networks:
• In Class A, 10.0.0.0 to 10.255.255.255.
• In Class B, 172.16.0.0 to 172.31.255.255.
• In Class C, 192.168.0.0 to 192.168.255.255.
No host with an IP address in the three ranges exists on the Internet. You can use those IP addresses in
an enterprise network freely without requesting them from an ISP or a registration center.
In addition to translating private addresses to public addresses, NAT can also perform address
translation between any two networks. In this document, the two networks refer to an internal network
and an external network. Generally a private network is an internal network, and a public network is an
external network.
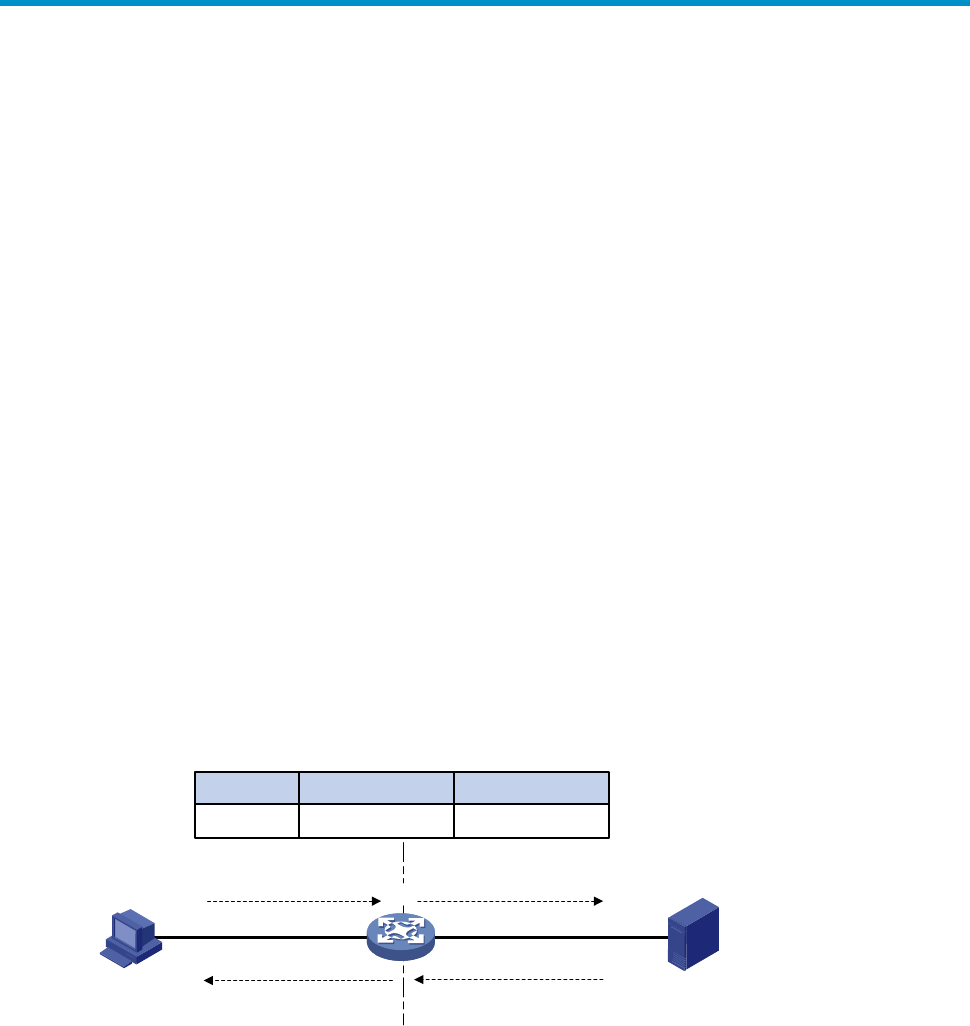
223HFigure 1 shows the NAT operation.
Figure 1 NAT operation
1. The internal host with IP address 192.168.1.3 sends an IP packet to the external server with IP
address 1.1.1.2 through the NAT device.
2. Upon receiving the packet, the NAT device checks the IP header and finds that it is destined to the
external network. The NAT device then translates the private address 192.168.1.3 to the globally
unique public address 20.1.1.1 and forwards the packet to the server on the external network.
Meanwhile, the NAT device adds the mapping of the two addresses into its NAT table.
3. The external server responds to the internal host with an IP packet whose destination IP address is
20.1.1.1. Upon receiving the packet, the NAT device checks the IP header, looks into its NAT
table for the mapping, replaces the destination address with the private address of 192.168.1.3,
and then sends the new packet to the internal host.
192.168.1.3
Src : 192.168.1.3
Dst : 1.1.1.2
Src : 20.1.1.1
Dst : 1.1.1.2
192.168.1.1 20.1.1.1
Src : 1.1.1.2
Dst : 20.1.1.1
Src : 1.1.1.2
Dst : 192.168.1.3
1.1.1.2
Server
Host
NAT
Intranet
Internet
Before NAT
192.168.1.3
After NAT
20.1.1.1
Direction
Outbound










