F3726, F3211, F3174, R5135, R3816-HP Firewalls and UTM Devices NAT and ALG Configuration Guide-6PW100
Table Of Contents
- Title Page
- Table of Contents
- Configuring NAT
- Overview
- Configuration guidelines
- Configuring NAT in the Web interface
- Recommended configuration procedure
- Creating an address pool
- Configuring dynamic NAT on an interface
- Creating a static address mapping
- Enabling static NAT on an interface
- Configuring an internal server
- Configuring ACL-based NAT on the internal server
- Configuring DNS mapping
- NAT configuration example
- Internal server configuration example
- Configuring NAT at the CLI
- NAT configuration task list
- Configuring static NAT
- Configuring dynamic NAT
- Configuring an internal server
- Configuring ACL-based NAT on an internal server
- Configuring DNS mapping
- Displaying and maintaining NAT
- One-to-one static NAT configuration example
- Dynamic NAT configuration example
- Common internal server configuration example
- NAT DNS mapping configuration example
- Troubleshooting NAT
- Configuring NAT-PT
- Feature and hardware compatibility
- Overview
- NAT-PT configuration task list
- Configuration prerequisites
- Enabling NAT-PT
- Configuring a NAT-PT prefix
- Configuring IPv4/IPv6 address mappings on the IPv6 side
- Configuring IPv4/IPv6 address mappings on the IPv4 side
- Setting the ToS field after NAT-PT translation
- Setting the traffic class field after NAT-PT translation
- Configuring static NAPT-PT mappings of IPv6 servers
- Displaying and maintaining NAT-PT
- NAT-PT configuration examples
- Troubleshooting NAT-PT
- NAT444
- Configuring ALG
- Support and other resources
- Index
63
Figure 51 Network diagram
149BConfiguration procedure
This section describes ALG configuration only, assuming that other required configurations on the server
and client have been done.
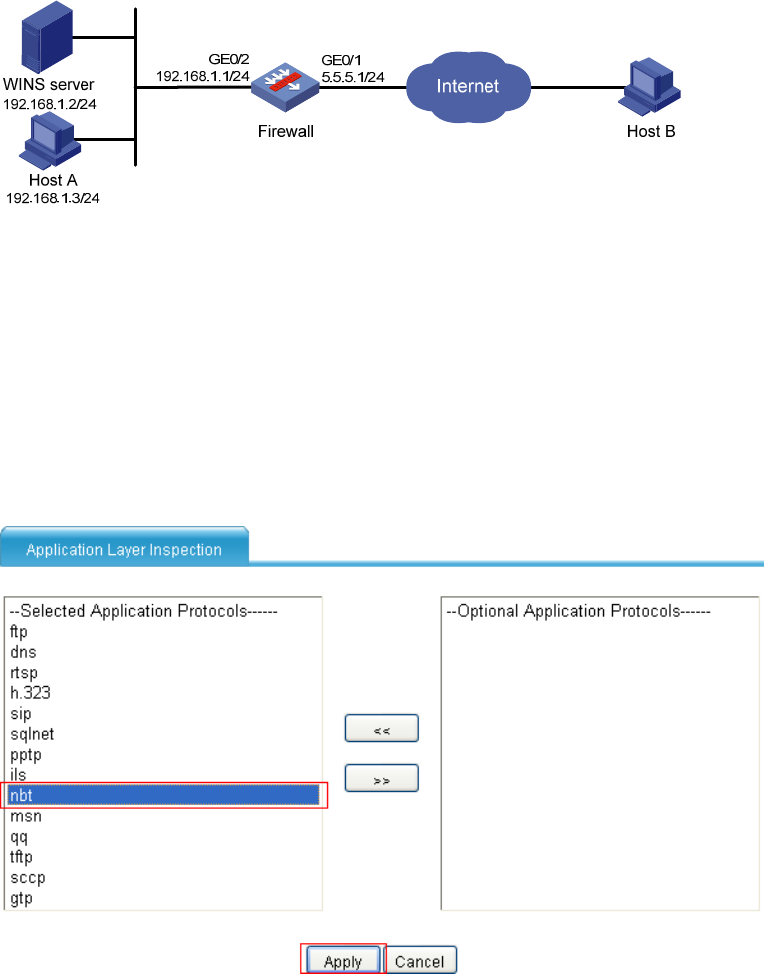
1. Enable ALG for NBT:
a. Select Firewall > ALG from the navigation tree.
b. Add nbt to the Selected Application Protocols list.
c. Click Apply.
Figure 52 Enabling ALG for NBT
2. Configure static NAT:
a. Select Firewall > NAT > Static NAT from the navigation tree.
b. In the Static Address Mapping area, click Add.
c. Enter 192.168.1.3 as the internal IP address.
d. Enter 5.5.5.9 as the global IP address.
e. Click Apply.










