F3726, F3211, F3174, R5135, R3816-HP Firewalls and UTM Devices System Management and Maintenance Configuration Guide-6PW100
178
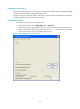
Figure 74 Specifying the host name (or IP address)
c. Click Open to connect to the server.
If the connection is successfully established, the system asks you to enter the username and
password. After entering the username (client001) and password (aabbcc), you can enter the
command-line interface of the server.
295BWhen the firewall acts as an Stelnet server for publickey
authentication
462BNetwork requirements
As shown in 899HFigure 75, you can log in to the firewall through the Stelnet client (SSH2) that runs on the host.
The firewall acts as the Stelnet server, adopting publickey authentication and the RSA public key
algorithm.
Figure 75 Network diagram