F3726, F3211, F3174, R5135, R3816-HP Firewalls and UTM Devices VPN Configuration Guide-6PW100
160
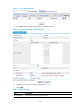
Figure 117 IPsec SAs
Table 13 Field description
Field Descri
p
tion
Source IP
IP address of the local end of the IPsec SA.
Destination IP
IP address of the remote end of the IPsec SA.
SPI SPI of the IPsec SA.
Security Protocol
Security protocol that the IPsec SA uses.
Authentication Algorithm
Authentication algorithm that the security protocol uses.
Encryption Algorithm
Encryption algorithm that the security protocol uses.
204BViewing packet statistics
Select VPN > IPSec > Statistics from the navigation tree to view packet statistics.
Figure 118 Packet statistics
205BIPsec configuration example
In this example, Device A is the firewall.
434BNetwork requirements
As shown in 773HFigure 119, an enterprise branch accesses the headquarters through IPsec VPN. Configure
the IPsec VPN as follows: