R3166-R3206-HP High-End Firewalls Access Control Configuration Guide-6PW101
171
The shared keys for authenticating authentication and authorization packets exchanged between the
NAS and the RADIUS server are both abc. The usernames sent to the RADIUS server carry no domain
names.
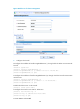
Figure 100 RADIUS authentication and authorization for Telnet users by a network device
Configuration procedure
# Configure an IP address for each interface as shown in Figure 100. The detailed configuration is
omitted here.
1. Configure the NAS
# Enable the Telnet server on Firewall A.
<FirewallA> system-view
[FirewallA] telnet server enable
# Configure Firewall A to use AAA for Telnet users.
[FirewallA] user-interface vty 0 4
[FirewallA-ui-vty0-4] authentication-mode scheme
[FirewallA-ui-vty0-4] quit
# Create RADIUS scheme rad.
[FirewallA] radius scheme rad
# Specify the IP address of the primary authentication server as 10.1.1.2, the port for authentication as
1645, and the shared key for authenticating authentication packets as abc.
[FirewallA-radius-rad] primary authentication 10.1.1.2 1645 key abc
# Specify the scheme to exclude the domain names from usernames to be sent to the RADIUS server.
[FirewallA-radius-rad] user-name-format without-domain
# Set the source IP address for outgoing RADIUS packets as 10.1.1.1.
[FirewallA-radius-rad] nas-ip 10.1.1.1
[FirewallA-radius-rad] quit
# Create ISP domain bbb.
[FirewallA] domain bbb
# Specify the authentication method for Telnet users as rad.
[FirewallA-isp-bbb] authentication login radius-scheme rad
# Specify the authorization method for Telnet users as rad.
[FirewallA-isp-bbb] authorization login radius-scheme rad