R3166-R3206-HP High-End Firewalls System Management and Maintenance Configuration Guide-6PW101
148
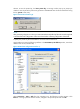
Figure 69 SSH client configuration interface 2)
In the window shown in Figure 69, click Open. If the connection is normal, you will be prompted to enter
the username. After entering the correct username (client002), you can enter the configuration interface
of Firewall.
SSH client configuration examples
When the firewall acts as a client for password authentication
Network requirements
• As shown in Figure 70, Firewall A (the SSH client) needs to log into Firewall B (the SSH server)
through the SSH protocol. The username of the SSH client is client001 and the password is aabbcc.
• Password authentication is required. The username and password are saved on the SSH server.
Figure 70 Firewall acts as client for password authentication
Configuration procedure
1. Configure the SSH server
# Create RSA and DSA key pairs and enable the SSH server.