R3204P16-HP Load Balancing Module Network Management Configuration Guide-6PW101
Table Of Contents
- Title page
- Contents
- Interface management configuration
- IP addressing configuration
- MAC address table configuration
- Layer 2 forwarding configuration
- Layer 2 forwarding overview
- Configuring general Layer 2 forwarding
- Configuring inline Layer 2 forwarding
- Configuring inter-VLAN Layer 2 forwarding
- Forward-type inline Layer 2 forwarding configuration example
- Blackhole-type inline Layer 2 forwarding configuration example
- Inter-VLAN Layer 2 forwarding configuration example
- VLAN configuration
- ARP configuration
- Gratuitous ARP configuration
- Proxy ARP configuration
- Layer 3 forwarding configuration
- NAT configuration
- Overview
- Configuring a NAT policy in the web interface
- Configuring NAT in the CLIs
- Configuration guidelines
- ALG configuration
- Static route configuration
- RIP configuration
- OSPF configuration
- BGP configuration
- Policy-based routing configuration
- Route displaying
- DNS configuration
- Overview
- Configuring DNS on the web interface
- Configuring DNS in the CLIs
- Troubleshooting IPv4 DNS configuration
- Support and other resources
- Index
108
• SQLNET (a language in Oracle)
• Trivial File Transfer Protocol (TFTP)
The following describes the operation of an ALG-enabled HP load balancing (LB) module, taking FTP as
an example. As shown in Figure 65, the ho
st in the outside network accesses the FTP server in the inside
network in passive mode through the LB module.
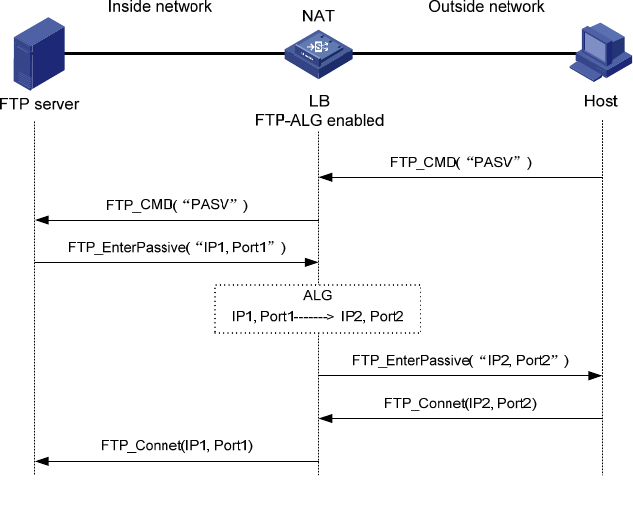
Figure 65 Network diagram for ALG-enabled FTP application in passive mode
The communication process includes the following stages:
1. Establishing a control connection
The host sends a TCP connection request to the server. If a TCP connection is established, the server and
the host enter the user authentication stage.
2. Authenticating the user
The host sends the server an authentication request, which contains the FTP commands (user and
password) and the contents.
When the request passes through the ALG-enabled LB module, the commands in the payload of the
packet will be resolved and used to check whether the state machine transition is going on correctly. If not,
the request will be dropped. In this way, ALG protects the server against clients that send packets with
state machine errors or log into the server with illegal user accounts.
An authentication request with a correct state is forwarded by the ALG-enabled LB module to the server,
which authenticates the host according to the information in the packet.
3. Establishing a data connection
If the host passes the authentication, a data connection is established between it and the server. If the
host is accessing the server in passive mode, the data connection process is different. In passive mode,
the server sends the host a PASV response that uses its private network address and port number (IP1,
Port1). When the response arrives at the ALG-enabled LB module, the LB module resolves the packet and
translates the server’s private network address and port number into the server’s public network address
and port number (IP2, Port2) respectively. Then, the module uses the public network address and port
number to establish a data connection with the host.










