R3204P16-HP Load Balancing Module Security Configuration Guide-6PW101
5
• The internal network is a trust network and can access the server and the external network. You can
deploy the internal network in the Trust zone with a higher priority and connect interface
Ten-GigabitEthernet 0/0.1 on the LB card to the external network.
• The external network is an untrusted network, and you need to use strict security rules to control
access from the external network to the internal network and the server. You can deploy the external
network in the Untrust zone with a lower priority and connect interface Ten-GigabitEthernet 0/0.2
on the LB card to the external network.
• If you deploy the WWW server and the FTP server on the external network, security cannot be
ensured; if you deploy them on the internal network, the external illegal users may use the security
holes to attack the internal network. Therefore, you can deploy the servers in the DMZ zone with a
priority between Trust and Untrust, and connect Ethernet interface Ten-GigabitEthernet 0/0.3 on
the LB card to the servers. In this way, the server in the DMZ zone can access the external network
in the Untrust zone with a lower priority, but when it accesses the internal network in the Trust zone
with a higher priority, its access is controlled by the security rules.
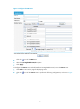
Figure 5 Network diagram for configuring zones
Configuration procedure
By default, the system has created the Trust, DMZ and Untrust zones, and you only need to deploy them.
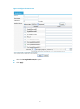
# Configure the Trust zone, and add interface Ten-GigabitEthernet 0/0.1 to the Trust zone.
• Select Security > Zone from the navigation tree and click the icon of the Trust zone to perform
the following configurations, as shown in Figure 6.