R3204P16-HP Load Balancing Module Security Configuration Guide-6PW101
9
Virtual fragment reassembly
NOTE:
The LB modules support virtual fragment reassembly in the web interface only.
Virtual fragment reassembly overview
To prevent service modules (such as NAT) from processing packet fragments that arrive out of order, you
can enable the virtual fragment reassembly feature. This feature can virtually reassemble the fragments
of a datagram through fragment checking, sequencing and caching so as to ensure that fragments arrive
at service modules in order.
The virtual fragment reassembly feature can also detect the following types of fragment attacks, and
discard the attack fragments for security.
• Tiny fragment attack: If the first fragment of a datagram is very small and the transport layer
protocol (such as TCP and UDP) header is in the second fragment, a tiny fragment attack is
considered.
• Overlapping fragment attack: If two consecutive incoming fragments are identical or overlapping,
an overlapping fragment attack is considered.
• Fragment-flood attack: If the maximum number of fragments per datagram or the maximum number
of fragment queues on the device is reached, a fragment-flood attack is considered.
Configuring virtual fragment reassembly
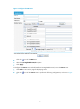
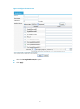
Select Security > Virtual Reassembly from the navigation tree to enter the virtual fragment reassembly
configuration page, as shown in Figure 9.
Figure 9 Virtual fragment reassembly configuration page