R3721-F3210-F3171-HP High-End Firewalls Attack Protection Configuration Guide-6PW101
26
3. If the source address is not found in the FIB table, URPF makes a decision based on the default
route and the allow-default-route option.
{ If the default route is available but the allow-default-route option is not selected, the packet is
rejected no matter which check approach is taken.
{ If the default route is available and the allow-default-route option is selected, URPF operates
depending on the check approach. In strict approach, URPF lets the packet pass if the outgoing
interface of the default route is the receiving interface, and otherwise rejects it. In loose
approach, URPF lets the packet pass directly.
4. A rejected packet will be filtered by an ACL, if specified. If the packet is permitted by the ACL, it
is forwarded as normal (such packets are displayed in the URPF information as "suppressed
drops"); otherwise, it is discarded.
Configuration procedure
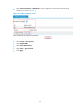
Select Intrusion Detection > URPF Check from the navigation tree to enter the URPF check configuration
page, as shown in Figure 29.
On this page, select a security zone to view and configure URPF check
settings for the security zone.
Figure 29 URPF check configuration page
Table 11 Configuration items
Item Descri
p
tion
Security Zone
Security zone where the URPF check is to be configured. URPF configuration takes
effect on all the interfaces in the security zone.
IMPORTANT:
URPF configuration takes effect on the packets received by the interfaces in the security
zone only.
Enable URPF
Enable/Disable URPF check.
If this box is not selected, URPF check is disabled and the following parameters are
not configurable.
By default, URPF check is disabled.
Allow Default Route Allow using the default route for URPF check.
ACL Reference an ACL.