R3721-F3210-F3171-HP High-End Firewalls System Management and Maintenance Configuration Guide-6PW101
147
NOTE:
• In the interaction stage, you can execute commands from the client by pasting the commands in text
format (the text must be within 2000 bytes). The commands must be available in the same view.
Otherwise, the server might not be able to perform the commands correctly.
• If the command text exceeds 2000 bytes, you can execute the commands by saving the text as a
configuration file, uploading the configuration file to the server through Secure FTP (SFTP), and then
using the configuration file to restart the server.
SSH connection across VPNs
With this function, you can configure the device as an SSH client to establish connections with SSH
servers in different MPLS VPNs.
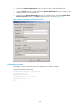
As shown in Figure 71, the ho
sts in VPN 1 and VPN 2 access the MPLS backbone through MCE, with the
services of the two VPNs isolated. After the MCE is enabled with the SSH client function, it can establish
SSH connections with CEs in different VPNs that are enabled with the SSH server function to implement
secure access to the CEs and secure transfer of log file.
Figure 71 Network diagram
Configuring the firewall as an SSH server
SSH server configuration task list
Task Remarks
Generating a DSA or RSA key pair Required.
Enabling the SSH server function Required.
Configuring the user interfaces for SSH clients Required.
Configuring a client public key
Required for publickey authentication users and
optional for password authentication users.
Configuring an SSH user Optional.
Setting the SSH management parameters Optional.
MCE
VPN 1
P
MPLS backbone
PE
PE
CE
VPN 2
VPN 2
SSH server
Host
Host
CE
VPN 1
SSH server
SSH client