R3721-F3210-F3171-HP High-End Firewalls System Management and Maintenance Configuration Guide-6PW101
155
Task Command
Remarks
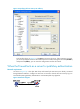
Display the mappings between
SSH servers and their host public
keys on an SSH client.
display ssh server-info [ | { begin | exclude |
include } regular-expression ]
Available in any
view
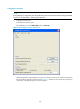
Display information about one or
all SSH users on an SSH server.
display ssh user-information [ username ] [ |
{ begin | exclude | include } regular-expression ]
Available in any
view
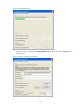
Display the public keys of the local
key pairs.
display public-key local { dsa | rsa } public [ |
{ begin | exclude | include } regular-expression ]
Available in any
view
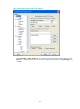
Display the public keys of the SSH
peers.
display public-key peer [ brief | name
publickey-name ] [ | { begin | exclude | include }
regular-expression ]
Available in any
view
SSH server configuration examples
When the Firewall acts as a server for password authentication
Network requirements
As shown in Figure 72, a host (the SSH client) and Firewall (the SSH server) are directly connected
through Ethernet interfaces. Configure an SSH user on Firewall so that the host can securely log in to
Firewall after passing password authentication. Configure a username and password for the user on
Firewall.
Figure 72 Network diagram
Configuration procedure
1. Configure the SSH server.
# Generate the RSA key pairs.
<Firewall> system-view
[Firewall] public-key local create rsa
The range of public key size is (512 ~ 2048).
NOTES: If the key modulus is greater than 512,
It will take a few minutes.
Press CTRL+C to abort.
Input the bits of the modulus[default = 1024]:
Generating Keys...
++++++++
++++++++++++++
+++++
++++++++
# Generate a DSA key pair.
[Firewall] public-key local create dsa