R3721-F3210-F3171-HP High-End Firewalls System Management and Maintenance Configuration Guide-6PW101
157
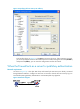
Figure 73 Specifying the host name (or IP address)
In the window shown in Figure 73, click Open to connect to the server. If the connection is normal,
you will be prompted to enter the username and password. After entering the username (client001)
and password (aabbcc), you can enter the configuration interface of Firewall.
When the Firewall acts as a server for publickey authentication
Network requirements
As shown in Figure 74, a host (the SSH client) and Firewall (the SSH server) are directly connected
through Ethernet interfaces. Configure an SSH user on Firewall so that the host can securely log in to
Firewall after passing publickey authentication. Use the RSA public key algorithm.
Figure 74 Network diagram