R3721-F3210-F3171-HP High-End Firewalls VPN Configuration Guide-6PW101
366
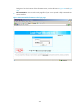
Figure 257 Adding a security policy
Table 57 Security policy configuration items
Item Descri
p
tion
Name Enter a name for the security policy.
Level
Set a level for the security policy. A larger number means a higher level.
If multiple security policies are defined, the system first uses the security policy with the
highest priority to check the user host. If the host does not satisfy the security policy, the
system uses the security policy with the second highest priority, and so forth until the
host satisfies a security policy or fails security check.
The resources that the user can access are those defined in the security policy that the
user first passes. Therefore, when you configure security policies, specify more
resources for a security policy that has a higher level.
Description Enter a description for the security policy.
Policy Configuration
Set check rules for the security policy.
Check rules fall into seven categories: operating system, browser, antivirus software,
firewall, certificate, file, and process.
To pass the check of a category, a host needs to satisfy at least one rule of the category.
To pass the check of a security policy, a host must satisfy all categories of the policy.
Click the expansion button before a category to view the rule information. Click the
Add button to add a rule for the category. For more information about rule
configuration, see Table 58.