R3721-F3210-F3171-HP High-End Firewalls VPN Configuration Guide-6PW101
397
Connection initialization phase
When a client accesses the server for the first time, connection initialization is performed first. During the
initialization procedure, the two parties negotiate whether VAM protocol packets should be secured. If so,
they negotiate the packet encryption and integrity validation algorithms, generate the keys, and
acknowledge the negotiated result. After the connection initialization process completes, the client
proceeds with the registration phase. Figure 297 sh
ows the initialization process.
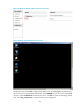
Figure 297 Initialization process
1. The client sends the server a connection request, which carries the supported encryption and
integrity validation algorithms.
2. Upon reception of the connection request, the server and the client begin to negotiate the
algorithms to be used, with the server dominating the negotiation. When negotiating an algorithm
to be used, the VAM server first compares the algorithm of the highest priority on its own algorithm
list against the algorithm list of the client. If a match is found, the algorithm is used. If not, the server
compares its next-highest priority algorithm against the list. The operation continues until a match
is found or all the algorithms on the server’s algorithm list have been compared. If a match is found,
the server sends to the client a connection response, which carries the negotiation result, and at the
same time, the server and the client generate the encryption key and integrity validation key.
3. The client and server respectively checks whether the algorithm negotiation and key negotiation
are successful through the negotiation acknowledge packets.
Registration phase
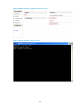
Figure 298 Registration process
Figure 298 shows the registration process:
1. The client sends the server a registration request, which carries information about the client.
2. Upon reception of the registration request, the server first determines whether to authenticate the
identity of the client. If identity authentication is not required, the server directly registers the client
and sends the client a registration acknowledgement. Otherwise, the server sends the client an