R21xx-HP FlexFabric 11900 IP Multicast Configuration Guide
Table Of Contents
- Title Page
- Contents
- Multicast overview
- Configuring IGMP snooping
- Overview
- IGMP snooping configuration task list
- Configuring basic IGMP snooping functions
- Configuring IGMP snooping port functions
- Configuring IGMP snooping policies
- Displaying and maintaining IGMP snooping
- IGMP snooping configuration examples
- Troubleshooting IGMP snooping
- Configuring multicast routing and forwarding
- Configuring IGMP
- Configuring PIM
- Overview
- Configuring PIM-DM
- Configuring PIM-SM
- Configuring common PIM features
- Displaying and maintaining PIM
- PIM configuration examples
- Troubleshooting PIM
- Configuring MLD snooping
- Overview
- MLD snooping configuration task list
- Configuring basic MLD snooping functions
- Configuring MLD snooping port functions
- Configuring MLD snooping policies
- Displaying and maintaining MLD snooping
- MLD snooping configuration examples
- Troubleshooting MLD snooping
- Configuring IPv6 multicast routing and forwarding
- Configuring MLD
- Configuring IPv6 PIM
- PIM overview
- Configuring IPv6 PIM-DM
- Configuring IPv6 PIM-SM
- Configuring common IPv6 PIM features
- Displaying and maintaining IPv6 PIM
- IPv6 PIM configuration examples
- Troubleshooting IPv6 PIM
- Support and other resources
- Index
2
In Figure 1, assume that Host B, Host D and Host E need the information. A separate transmission channel
must be established from the information source to each of these hosts.
In unicast transmission, the traffic transmitted over the network is proportional to the number of hosts that
need the information. If a large number of hosts need the information, the information source must send
a separate copy of the same information to each of these hosts. Sending many copies can place a
tremendous pressure on the information source and the network bandwidth.
Unicast is not suitable for batch transmission of information.
Broadcast
In broadcast transmission, the information source sends information to all hosts on the subnet, even if
some hosts do not need the information.
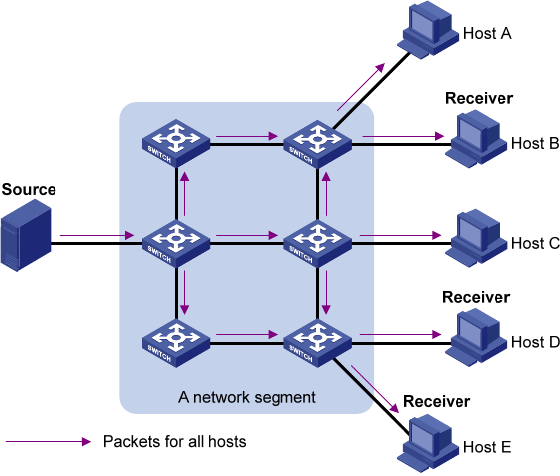
Figure 2 Broadcast transmission
In Figure 2, assume that only Host B, Host D, and Host E need the information. If the information is
broadcast to the subnet, Host A and Host C also receive it. In addition to information security issues,
broadcasting to hosts that do not need the information also causes traffic flooding on the same subnet.
Broadcast is not as efficient as multicast for sending data to groups of hosts.
Multicast
Unicast and broadcast techniques cannot provide point-to-multipoint data transmissions with the
minimum network consumption.
Multicast transmission can solve this problem. When some hosts on the network need multicast
information, the information sender, or multicast source, sends only one copy of the information.
Multicast distribution trees are built through multicast routing protocols, and the packets are replicated
only on nodes where the trees branch.










