BLADE OS™ Application Guide HP GbE2c Ethernet Blade Switch for c-Class BladeSystem Version 5.1 Advanced Functionality Software
Table Of Contents
- Contents
- Figures
- Tables
- Preface
- Part 1: Basic Switching
- Accessing the Switch
- The Management Network
- Local Management Using the Console Port
- The Command Line Interface
- Remote Management Access
- Client IP Address Agents
- Securing Access to the Switch
- Setting Allowable Source IP Address Ranges
- RADIUS Authentication and Authorization
- TACACS+ Authentication
- LDAP Authentication and Authorization
- Secure Shell and Secure Copy
- Configuring SSH/SCP Features on the Switch
- Configuring the SCP Administrator Password
- Using SSH and SCP Client Commands
- SSH and SCP Encryption of Management Messages
- Generating RSA Host and Server Keys for SSH Access
- SSH/SCP Integration with Radius Authentication
- SSH/SCP Integration with TACACS+ Authentication
- End User Access Control
- Ports and Trunking
- Port-Based Network Access Control
- VLANs
- Spanning Tree Protocol
- RSTP and MSTP
- Link Layer Discovery Protocol
- Quality of Service
- Accessing the Switch
- Part 2: IP Routing
- Basic IP Routing
- Routing Information Protocol
- IGMP
- OSPF
- OSPF Overview
- OSPF Implementation in BLADE OS
- OSPF Configuration Examples
- Remote Monitoring
- Part 3: High Availability Fundamentals
- High Availability
- Layer 2 Failover
- Server Link Failure Detection
- VRRP Overview
- Failover Methods
- BLADE OS Extensions to VRRP
- Virtual Router Deployment Considerations
- High Availability Configurations
- High Availability
- Part 4: Appendices
- Index
BLADE OS 5.1 Application Guide
242 Chapter 14: High Availability BMD00113, September 2009
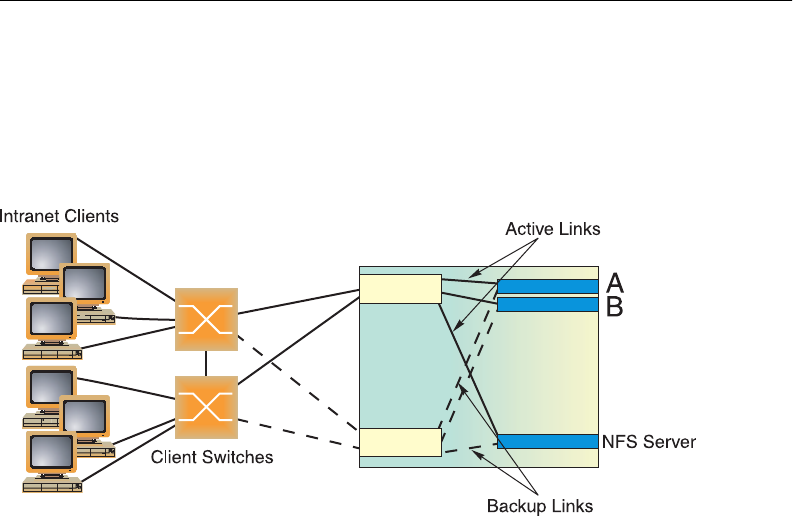
Failover Methods
With service availability becoming a major concern on the Internet, service providers are
increasingly deploying Internet traffic control devices, such as application switches, in redundant
configurations. Traditionally, these configurations have been hot-standby configurations, where
one switch is active and the other is in a standby mode. A non-VRRP hot-standby configuration is
shown in the figure below:
Figure 31 A Non-VRRP, Hot-Standby Configuration
While hot-standby configurations increase site availability by removing single points-of-failure,
service providers increasingly view them as an inefficient use of network resources because one
functional application switch sits by idly until a failure calls it into action. Service providers now
demand that vendors' equipment support redundant configurations where all devices can process
traffic when they are healthy, increasing site throughput and decreasing user response times when
no device has failed.
BLADE OS high availability configurations are based on VRRP. The BLADE OS implementation
of VRRP includes proprietary extensions.
Based on proprietary BLADE OS extensions to VRRP, BLADE OS supports Active-Active high
availability.
Primary Switch
IP: 200.200.200.100
Secondary Switch
IP: 200.200.200.101
Internet
Servers










