BLADE OS™ Application Guide HP GbE2c Ethernet Blade Switch for c-Class BladeSystem Version 5.1 Advanced Functionality Software
Table Of Contents
- Contents
- Figures
- Tables
- Preface
- Part 1: Basic Switching
- Accessing the Switch
- The Management Network
- Local Management Using the Console Port
- The Command Line Interface
- Remote Management Access
- Client IP Address Agents
- Securing Access to the Switch
- Setting Allowable Source IP Address Ranges
- RADIUS Authentication and Authorization
- TACACS+ Authentication
- LDAP Authentication and Authorization
- Secure Shell and Secure Copy
- Configuring SSH/SCP Features on the Switch
- Configuring the SCP Administrator Password
- Using SSH and SCP Client Commands
- SSH and SCP Encryption of Management Messages
- Generating RSA Host and Server Keys for SSH Access
- SSH/SCP Integration with Radius Authentication
- SSH/SCP Integration with TACACS+ Authentication
- End User Access Control
- Ports and Trunking
- Port-Based Network Access Control
- VLANs
- Spanning Tree Protocol
- RSTP and MSTP
- Link Layer Discovery Protocol
- Quality of Service
- Accessing the Switch
- Part 2: IP Routing
- Basic IP Routing
- Routing Information Protocol
- IGMP
- OSPF
- OSPF Overview
- OSPF Implementation in BLADE OS
- OSPF Configuration Examples
- Remote Monitoring
- Part 3: High Availability Fundamentals
- High Availability
- Layer 2 Failover
- Server Link Failure Detection
- VRRP Overview
- Failover Methods
- BLADE OS Extensions to VRRP
- Virtual Router Deployment Considerations
- High Availability Configurations
- High Availability
- Part 4: Appendices
- Index
BLADE OS 5.1 Application Guide
256 Appendix A: Troubleshooting BMD00113, September 2009
Port Mirroring
The port mirroring feature in the BLADE OS allows you to attach a sniffer to a monitoring port that
is configured to receive a copy of all packets that are forwarded from the mirrored port. BLADE OS
enables you to mirror port traffic for all layer 2 and layer 3. Port mirroring can be used as a
troubleshooting tool or to enhance the security of your network. For example, an IDS server can be
connected to the monitor port to detect intruders attacking the network.
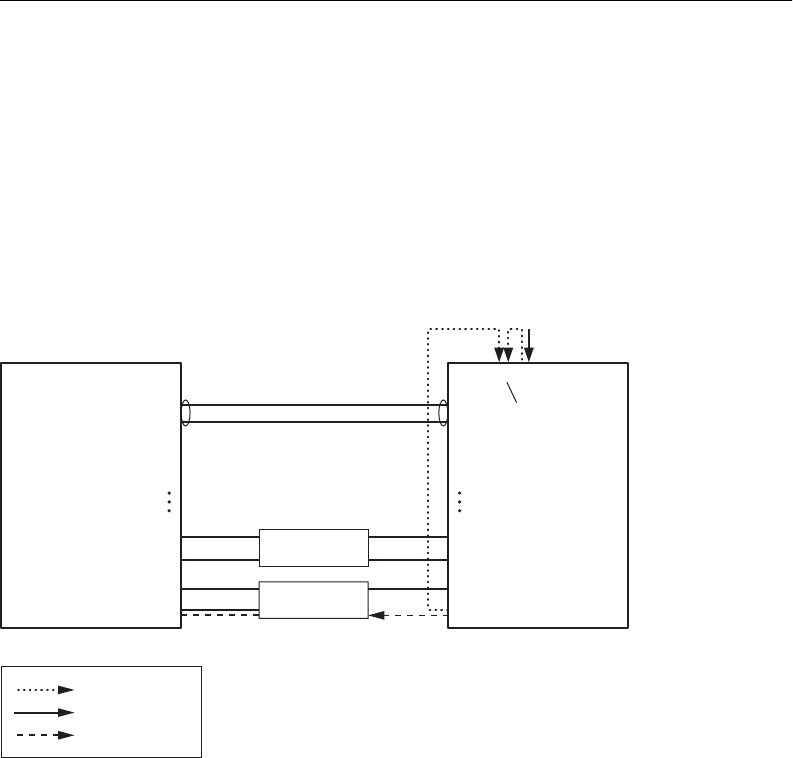
As shown in Figure 34, two mirrored ports (port 1 and port 21) are monitored by a single port (port
20). Similarly, you can have one port or many ports mirrored to the monitored port. Because the
switch presently supports only one monitor port, a single port being cannot be monitored by
multiple ports.
Figure 34 Mirroring Ports
Ingress and egress traffic is duplicated and sent to the monitor port after processing.
Port Mirroring Restrictions
The following restrictions apply for port mirroring:
Management port 19 cannot be configured as a port monitor.
Management VLAN 4095 traffic cannot be mirrored.
LACPDU packets cannot be mirrored.
Egress traffic
Mirrored traffic
Ingress traffic
Egress traffic
Legend
Switch 1
18
16
15
17
2
1
18
17
2
1
Server 1
4
3
4
3
Server 2
10/100/1000 Cross-Connects
Switch 2
Monitor:
Port 20
20 21 22 23 24 20 21 22 23 24
16
15










