NonStop SOAP 4.1 User's Manual
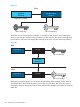
Figure 19
52ED879E
70F71D92
Big Random Number
Alice’s Public Key Alice’s Private Key
Key Generation
Function
Alice
These keys are used to encrypt the messages. For example, if Bob wants to send a message to
Alice, he can encrypt a message using her public key. Alice can then decrypt this message using
her private key. Only Alice can decrypt this message as she is the only one with the private key.
Figure 20
Alice’s Public Key
Hello Alice!
Encrypt
6EB69570
08E03CE4
Alice’s Private Key
Hello Alice! Decrypt
Alice
Bob
Messages can also be signed. You can ensure the authenticity of the message. If Alice wants to
send a message to Bob, and Bob wants to be sure that it is from Alice, then Alice can sign the
message by using her private key. Bob can then verify that the message is from Alice by using her
public key.
272 WS–Security in NonStop SOAP 4